TP-Link WA901N - Journey to serial access
This post contains detailed information about a security research that i have been conducting on a TP-Link WA901N router. All information is for education purpose only. I shared this post so that anyone interested in testing this device does not need to waste time getting access to its internal system.

WARNING: Keep in mind that some operations may permanently damage your device if not performed correctly. Proceed at your own risk!
Intro
I recently got access to a TP-Link WA901N which I intend to use for a side project, but before that and since I am relatively new to hardware hacking, I thought it would be interesting to try to gain access to its internal system and documenting the journey so I could share it with anyone interested in testing this device.
Getting shell access
After opening up the device I started inspecting the PCB looking for exposed interfaces that I could use as an entry point to the router internal system and I found 4 pin through holes that could possibly be a UART interface.
With the router turned off and using a multimeter’s continuity test function, I tested all pins through holes against a known ground (I just used the router CPU metal cover… it worked). Only one made my multimeter beeped so that was GND.
With the router turned on I confirmed that all the other through holes had voltage and decided to solder 4 pin headers to the PCB.

Using a USB to TTL module I connected to GND and then, with the router turned on, I connected the RX to each of the other pins until I found the one that printed boot information. There are other methods to find the correct pin layout, like using the multimeter or a logic analyzer, but in this case since there are only 3 possible pins it is easier and quicker this way.

So the correct pin layout is:

The command I used to connect was sudo picocom -b 115200 /dev/ttyUSB0 (note the baud rate for this router is 115200)
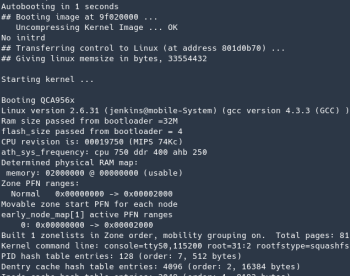
Once the boot process finished, I got a login prompt requesting a username and password. I tried several default and common login credentials, but no luck so I decided to move on in order to try to find something else that would help me get into the system.
Getting the firmware
During the initial PCB inspection, I also found an SPI flash memory near the UART through holes. These chips, specifically the ones near the UART interface, usually contain the device filesystem.
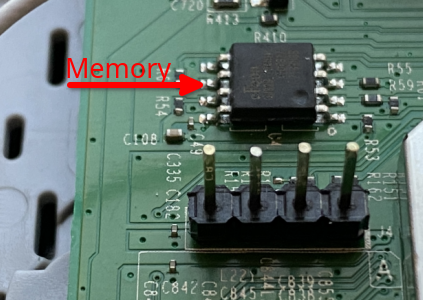
The quickest way to test this was to use a CH341A programmer with a test clip to try to dump the memory content.

I connected the test clip to the SPI memory - keep in mind that all pins must be aligned, which is easily achieved by matching the pin 1 on the SPI memory (marked with a dot) with the pin 1 in the test clip (red wire)


With everything set, I ran the following command sudo flashrom --programmer ch341a_spi -r firmware.bin to extract the memory contents into a file called firmware.bin
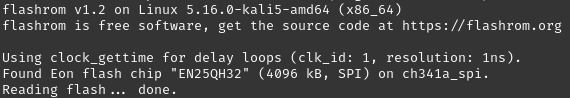
Analyzing the file with binwalk I got confirmation that this was really the router filesystem
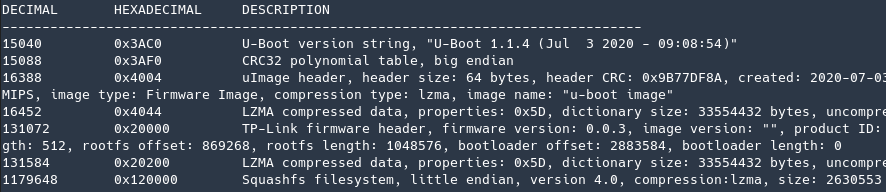
Once again using binwalk with the flag “-e” to extract its contents gave me access to the filesystem which I immediately started exploring, searching for useful information.
Since login credentials were my main goal, one the first files I looked for was the shadow file that is located in the /etc directory since it contains the users encrypted password. There was only one user (root) and the password was in MD5crypt
root:$1$GTN.gpri$DlSyKvZKMR9A9Uj9e9wR3/:15502:0:99999:7:::
The next step was to try to crack the root password, so I used hashcat to perform a dictionary attack using several known lists from SecList
After multiple failed attempts, I decided to brute force it, and while the attack was running I did a quick google search for that encrypted password and found several results! Apparently this is an old known password used by TP-Link (at least since 2013) but for some reason it is not in any common password dictionary (like SecList).
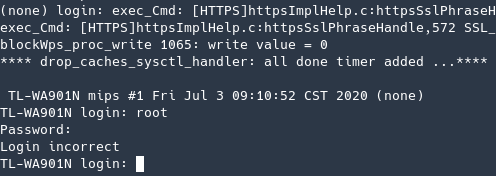
Anyway, the credentials are root:sohoadmin.
Root login
Now that I got the root password I could go back to the UART shell and try to login… and it worked!
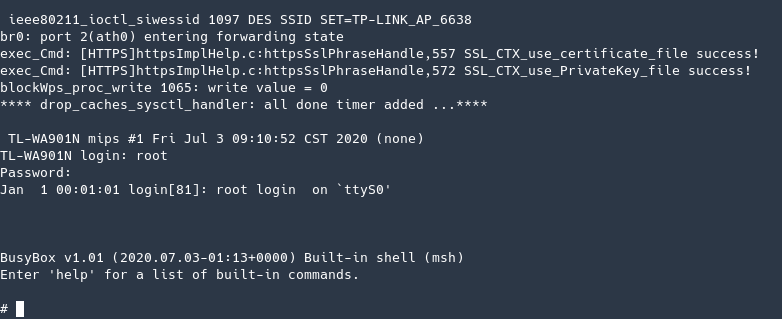
Next steps
Taking advantage of this root access, I will keep on digging in order to figure out if there is any vulnerability with this device and if anything comes up I will update this post.